The following article was originally published on the Oracle website and was originally done by Rasmus Lerdorf. Oracle published a number of articles about PHP to promote the language in combination with the Oracle database. A number of articles about PHP and Oracle can also be found on terminalcult.org
PHP's creator offers his thoughts on the PHP phenomenon, what has shaped and motivated the language, and where the PHP movement is heading
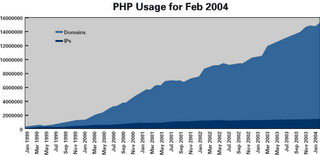
PHP is everywhere. In its February 2004 Web server survey, Netcraft poked 47,173,415 domains and found that 15,205,474 had PHP installed. That is approximately 32 percent of all domains on the Web, and there is no sign of its slowing down.
 The Early Days of PHP
The Early Days of PHP
I started developing PHP nearly 10 years ago now. That was long before the term "Open Source" was coined and before the GPL and Free Software was well known. And as with many open source projects that have gone on to become popular, the motivation was never philosophical or even narcissistic. It was purely a case of needing a tool to solve real-world Web-related problems. In 1994 the options were fairly limited when it came to Web development tools. I found myself writing dynamic components for Web sites in C or Perl, and the code overlap from one problem to the next was quite significant. For performance reasons, I was increasingly tending away from Perl and toward C, because the fork+exec overhead of having to run Perl as a standalone CGI was too restrictive.
The initial unreleased version of PHP was mostly a C library of common C functions I had written to be easily reusable from one open source project to the next. I had a simple state-machine-driven parser that picked tags out of HTML files and called the back-end C functions I had written. This code was initially released to the public as a package called Personal Home Page Tools, and each tool in the package was an example of how to use the system to solve a common problem on a personal home page. At some point along the way, I split out a piece and called it FI, for Form Interpreter. The idea behind FI was that it could do all the common things you needed to do when you received the result of a form submit. Some early examples:
[01] <!--getenv HTTP_USER_AGENT-->
[02] <!--ifsubstr $exec_result Mozilla-->
[03] Hey, you are using Netscape!<p>
[04] <!--endif-->
[05]
[06] <!--sql database select * from table where user='$username'-->
[07]
[08] <!--ifless $numentries 1-->
[09] Sorry, that record does not exist<p>
[10] <!--endif exit-->
[11]
[12] Welcome <!--$user-->!
[13] You have <!--$index:0--> credits left in your account.<p>
[14]
[15] <!--include /text/footer.html-->
My parser for FI was terrible, which prompted me to try to write a better one. I moved away from the syntax and went to instead, recombined parts of the Personal Home Page Tools with this new FI tool, and released that as a package called PHP/FI (the name was a bit of a tongue-in-cheek play on TCP/IP) in late 1995. PHP/FI grew right along with the Web over the next couple of years. In 1997 two guys in Israel, Zeev Suraski and Andi Gutmans, who were using PHP/FI asked if I would be interested in using a new parsing engine that they would write for the next version of PHP. I gathered up a few other people who had been sending patches and code for PHP/FI and we all coordinated to release PHP version 3 in mid-1998. This was probably the most crucial moment during the development of PHP. The project would have died at that point if it had remained a one-man effort and it could easily have died if the newly assembled group of strangers could figure out how to work together towards a common goal. We somehow managed to juggle our egos and other personal events and the project grew. The number of contributors has grown steadily and today we are pushing towards a release of PHP 5.0 sometime in the first half of 2004.
The Ugly Duckling of Programming Languages
Popular opinion about PHP is polarized. Language purists tend not to like the somewhat haphazard implementation of many features and some of the inconsistencies that have emerged over the years. At the same time, pragmatic problem solvers tend to love how PHP seems to almost read your mind and present itself as the perfect Web problem solving tool.
Among the things that drive the purists crazy are that names of functions are not case-sensitive but variables are; built-in functions are not consistently named; and no real structure is enforced on PHP developers, making it easy to write messy code. I can't really argue with these criticisms, but I can at least attempt to explain how and why we got to this state.
First, regarding the function-name case-sensitivity issue: This goes back to the very first version of PHP. In the early days of the Web, long before XHTML, it was very common for all HTML markup tags to be uppercase. But because these tags were not case-sensitive, people weren't very consistent about this. I wanted people to treat the special PHP tags as being basically just like other markup tags, which meant that PHP's tags should also not be case-sensitive. As PHP became more advanced and received features such as variables, it didn't hurt to make these new features case-sensitive, because it didn't break backward compatibility with existing PHP pages. Going back and suddenly making the initial simple tags, which were in essence just function calls, case-sensitive would have broken those pages and made them unusable in newer versions of PHP. People shouldn't have functions whose names differ only in case, anyway. Still, in retrospect, it would have been a good idea to break backward compatibility early on, when relatively few people were using PHP, but at the time, nobody could have predicted the amazing growth of PHP.
As to function naming itself, I tended to steal/borrow ideas from other languages and APIs I was familiar with. This means that PHP has functions such as strlen( and substr(), which would look silly if written as str_len() or sub_str(). I added things like stripslashes(), which, because of the length, is often written as StripSlashes() to make it easier to read. At the same time, I mimicked low-level database APIs, with functions such as msql_connect()—miniSQL was the first database to be supported by PHP—which used underscore naming. People familiar with these various sources were quite at home with the naming in PHP. PHP was never so much a standalone language as it was an interface between the Web server and all the various back-end tools you wanted to hook into the Web server. Consequently, when people look at PHP today as a standalone language without taking its context into account, it can appear somewhat inconsistent.
About the lack of enforced structure, all I can say is that I absolutely hate programming frameworks that lock me into a certain way of approaching a problem. That doesn't mean I don't believe in structure and frameworks, but I do believe in people having the power to come up with their own to match their environment. More on this later in the article, when I discuss possible architectures for your various PHP projects.
What it all boils down to is that PHP was never meant to win any beauty contests. It wasn't designed to introduce any new revolutionary programming paradigms. It was designed to solve a single problem: the Web problem. That problem can get quite ugly, and sometimes you need an ugly tool to solve your ugly problem. Although a pretty tool may, in fact, be able to solve the problem as well, chances are that an ugly PHP solution can be implemented much quicker and with many fewer resources. That generally sums up PHP's stubborn function-over-form approach throughout the years.
Advice for Architects
The most popular deployment model for PHP is for it to be linked directly into the preforking multiprocess Apache 1.3.x Web server. Unlike with Java, there is no standalone process like the JVM. PHP is similar to scripting languages such as Perl and Python in that it parses and executes scripts directly.
The lack of a central control process is a feature and at the same time a source of great frustration for many. The shared-nothing architecture of PHP where each request is completely distinct and separate from any other request leads to infinite horizontal scalability in the language itself. PHP encourages you to push scalability issues to the layers that require it. If you need a shared datastore, use a database that supports replication and can scale to the levels you need. If you need to load balance requests or distribute certain requests to certain servers, use a front end load balancer that supports this. By avoiding a central controlling process, PHP avoids being the bottleneck in the system. This is the defining characteristic that separates PHP from what people commonly refer to as application servers.

In the diagram above, one or more load balancers distribute incoming requests across any number of Web servers. For data storage, you might deploy a read-only database replica on each Web server if your dataset is small enough to let you do that, or you might create a separate tree of database servers to handle various types of requests.
Adding Structure
One of the big strengths of PHP over many other tools aimed at solving the Web problem is that other tools tend to associate such very specific targeted problem solving with the need to control how users approach the problem structurally. PHP doesn't impose any such structure, choosing instead to focus on making each individual functionality aspect of the problem as easy as possible to use. For example, PHP provides very targeted functions for communicating with a back-end database. These are specific to each database and do not sacrifice any performance to gain uniformity or consistency with other back-end databases. There is also no set way to structure a PHP application in terms of file layout and what goes where.
The fact that PHP doesn't impose structure doesn't mean that you shouldn't build your PHP applications in an organized and structured way. Here is one approach I like to show people who ask me how I would go about structuring a large PHP application.
+--------------------------------+
| HTML TEMPLATES |
| $DOC_ROOT/*.php |
+--------------------------------+
| TEMPLATE HELPERS |
| $DOC_ROOT/*.inc |
+--------------------------------+
| BUSINESS LOGIC |
| /usr/local/php/*.inc |
+--------------------------------+
| C/C++ CORE CODE |
| /usr/local/lib/php/*.so |
+--------------------------------+
This four-layer approach addresses a couple of issues. First, it separates the content along the lines of responsibility in a typical project. The Web front-end developers work from the top, and the back-end engineers work from the bottom. They overlap a bit in the template helpers layer. It also separates anything that contains HTML, by putting those files into the document_root and anything that doesn't contain HTML outside the document_root.
The top template layer typically contains very little PHP—just simple function calls and the odd include. Perhaps a loop. These files are usually edited with an HTML authoring tool. The second layer, the template helpers, is where the interface between the business logic and the layout is defined. This layer might have convenience functions such as start_table(), show_user_record(), and any other reusable component that makes template authors' lives easier.
The business-logic layer does not contain any HTML at all. This is where such things as SQL queries and any other PHP user-space business logic is implemented. You might expect to see a function such as get_user_record() implemented in this layer. This function would take an ID, perform the appropriate SQL query, and then return an associative array with the result. A function in the layer above then takes this array and wraps some HTML around it to make it look nice.
The final C/C++ layer is where you put any custom back-end code required for a project. Many people will not have anything for this layer, but if you have a proprietary C or C++ library, you can write a PHP extension to interface to that here. Sometimes this layer is also used when a business-logic function written in user-space PHP turns out to be too slow.
Hiring and Training PHP Developers
PHP is not a new language. It doesn't introduce any new concepts. This means that training programmers who already know any C, C++, Perl, or even Java to write PHP code is quite easy. I tend to look for people with C or C++ skills when I go looking for PHP developers for a project, the thinking being that you are much better off hiring experienced programmers than you would be if you hired someone who necessarily knows a lot about PHP. If they can handle those languages, PHP will be trivial for them. Of course, if they have experience with both, so much the better.
Deploying PHP Everywhere
Use the right tool for the job. I have run across companies that have completely bought into PHP, deploying it absolutely everywhere, but it was never meant to be a general-purpose language appropriate for every problem. It is most at home as the front-end scripting language for the Web. Depending on the traffic the Web site gets, it can be used to do the bulk of the back-end work as well. But at a certain point, you are going to need to write part of your code in a strongly typed, compiled language such as C or C++ for optimal performance.
Where Is PHP Going?
People are always asking me what lies ahead for PHP. That is a very difficult question to answer, because PHP is mostly a reactive open source project, in that it evolves to meet the needs of its community. In PHP5, the OO capabilities and integration with XML have been improved greatly. We have integrated an interesting tool called SQL-Lite, which provides a SQL interface directly to a file without requiring a server. It is not a replacement for a real database, obviously, but using it is certainly a much better approach than trying to write your own flat-file manipulation routines. And the fact that it gives you a SQL interface means that migration to a real database becomes easier if that is ever required.
These changes in PHP5, although significant, are evolutionary. We are not turning the world of PHP upside down with this release. Of the scripts written for PHP4, 99 percent will work unchanged in PHP5. The biggest change is that objects are handled differently in PHP5. When you new an object in PHP5, you now, by default, get a reference to that object that you can pass around without explicitly stating that you want the object passed by reference, as you had to in PHP4. If you actually want a copy of the object in PHP5, you need to "clone" it.
Longer-term, there are people exploring the use of the Parrot engine. Parrot was written as the engine behind Perl6, but it is really a language-neutral general-purpose scripting engine. It would be very interesting if the various scripting languages could all agree on a single back-end engine, which could then be used as a basis for common extensions and much better language interaction.
And still others are exploring Java connectivity through JSR 223, with some thinking that Java can be the single universal back end for scripting languages.
Despite what the future may hold for PHP, one thing will remain constant. We will continue to fight the complexity to which so many people seem to be addicted. The most complex solution is rarely the right one. Our single-minded direct approach to solving the Web problem is what has set PHP apart from the start, and while other solutions around us seem to get bigger and more complex, we are striving to simplify and streamline PHP and its approach to solving the Web problem.
Rasmus Lerdorf (rasmus@lerdorf.com) was born in Godhavn/Qeqertarsuaq on Disko Island off the coast of Greenland in 1968. He has been dabbling with UNIX-based solutions since 1985. Known for having gotten the PHP project off the ground in 1995, the mod_info Apache module and he can be blamed for the ANSI92 SQL-defying LIMIT clause in mSQL 1.x which has now, at least conceptually, crept into both MySQL and PostgreSQL.
He tends to deny being a programmer, preferring to be seen as a techy adept at solving problems. If the solution requires a bit of coding and he can't trick somebody else into writing the code, he will (very) reluctantly give in and write it. He is currently an infrastructure engineer at Yahoo! Inc. in Sunnyvale, California.
Some time ago I published a paper on my website about a bug in Oracle Store. Now I like to repost it on my weblog also. The bug is a combination of bad coding from the side of Oracle and not applied security settings. When the bug is exploited a user is able to view all the orders ever placed in an oracle iStore installation.
For those who are not aquatinted with Oracle iStore, iStore is the Oracle webshop application.
Preface:
Current versions of Oracle iStore have a known bug, which enables users to view orders in order tracker placed by other customers. The root cause is bad coding from Oracle. When a order is queried from the Oracle iStore order tracker the only reference key is the order number.
Reproducing the problem:
Login to Oracle iStore and go to the order tracker page [/ibeCOtdOrdSumMain.jsp?a=b]. This page will give you an overview containing all the orders placed by this customer. When selecting one of the orders the number parameters will change and [ibeCOtdOrdSumMain.jsp] will contain the following parameters and possibly the following values depending on your implementation: ?qsr=0&qob=5&qia=false&qc0=13&qo0=AIS&qv0=4077&qa=details&qid=
If qid contains a long string of alphanumeric characters you have encryption enabled however if it contains a numeric string your iStore implementation is vulnerable of URL manipulation.
If qid contains a numeric string you can shift between orders by changing the number. This will enable the user to view ALL orders available in IBE_ORDER_HEADER_V.
Root cause:
When a order detail page is queried iStore is executing the following query where the value of qid relates to the column HEADER_ID in IBE_ORDER_HEADER_V. This is the only binding value between the record and the user request. There is no validation done to determine if the order is placed by the same customer as the one requesting the details of the order.
Quick fix:
Preventing the user from manipulating the URL is to enable encryption to encrypt the parameter values used in the URL. This is a standard functionality. To enable the encryption take the following steps:
(1) Login to Oracle e-business suite using the sysadmin account.
(2) Go to Setings - System - Cookies.
(3) Make sure there is a value entered in the [Encryption Key] field. If not enter a random encryption key.
(4) Reboot and check if the URL parameters are encrypted. Please note NOT ALL parameters will be encrypted.
NOTE:
It is possible that you have done some customizations to Oracle iStore which will cause errors after enabling encryption. The reason for this is that you probably do not a decrypt function for some of the parameters which are now encrypted. This results in iStore trying to use the encrypted strings as a value instead of using the real decrypted value. (Example: instead of using the values 5 it is now using the value G57FHSYEGE3H2J83GA8E3K3H37)
If this is the case you will have to add decryption and encryption routines into your code to make it work with the new encryption. The best way to do this is to catch this in a if statement which enables you to create code that will encrypt and decrypt only if the encryption option is turned on. This will prevent you from having to change code again if you ever have to turn encryption off again.
Please find an example of this below:
//If encryption is active encrypt URL parameter.
String retrieveKey = SiteProperty.getValue("cookie_encryption_key");
IBEUtil.log("ibeCOtdOrdSumMain.jsp","retrieve Key = "+retrieveKey);
if (retrieveKey != null)
{
pageContext.setAttribute("retrieveKey",retrieveKey,PageContext.REQUEST_SCOPE);
}
String key = (String)pageContext.getAttribute("retrieveKey",PageContext.REQUEST_SCOPE);
String xxEncOrder_number = cartIdStr;
if (key != null && cartIdStr != null )
{
AolSecurity security = new AolSecurity();
xxEncOrder_number = security.encrypt(key, cartIdStr,cartIdStr.length());
}
Stable fix:
To fix this in a stable way you will have to change a little more. The enabling of the encryption is a good thing, and advertised and promoted by Oracle in their implementation guide. However a better fix is to change the query and the way the query is called. The best way is to add a check on customer ID to make sure that the customer requesting the details of the order is the same customer who placed the order.
A couple of days ago I reported on sentinella, a armed robot made by Samsung(). I told in that story that this was the/one of the first robots that whould be armed and therfor was in violation with the rules of robotics which are set by Isaac Asimov.
After some more research I learned that there are a lot more robots that are violating this set of rules. A good example is the Foster-Miller company which has a line of armed robots named TALON robots
 TALON robots can be configured with M240 or M249() machine guns or Barrett 50-caliber rifles for armed reconnaissance missions. A prototype system was delivered to the 3/2 Stryker brigade for evaluation, and successful testing was performed by the brigade in Kuwait in December 2003. Additional prototypes have been manufactured and are currently undergoing system safety certification by the U.S. Army. Alternative weapons, including 40 mm grenade launchers and anti-tank rocket launchers, continue to be evaluated by the U.S. Army.
TALON robots can be configured with M240 or M249() machine guns or Barrett 50-caliber rifles for armed reconnaissance missions. A prototype system was delivered to the 3/2 Stryker brigade for evaluation, and successful testing was performed by the brigade in Kuwait in December 2003. Additional prototypes have been manufactured and are currently undergoing system safety certification by the U.S. Army. Alternative weapons, including 40 mm grenade launchers and anti-tank rocket launchers, continue to be evaluated by the U.S. Army.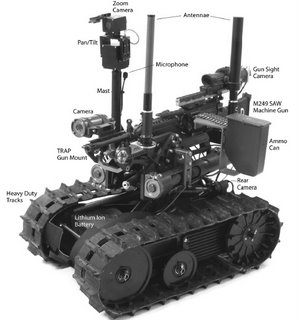
Today China, the European Union, India, Japan, Russia, the United States and South Korea have signed the an agreement for the development of a international experimental thermonuclear reactor. The project named ITER will be constructed in Cadarache, southern France, and will start in 2008, the planned cost are around 10 billion Euros. Negotiations started in 1996 and are finished as from today.
ITER will do research on nuclear fusion and a way to make this available outside a research environment. You can see the scale of the reactor if you click on the image, the man at the bottom of the reactor indicates it total size.
 Even do the project is quite ambitious the ITER project will not be the first to successfully build a nuclear fusion reactor, today Thiago Olson, a 17 old student reported that he build a reactor in the basement of his parents and scientists have found his reports true.
Even do the project is quite ambitious the ITER project will not be the first to successfully build a nuclear fusion reactor, today Thiago Olson, a 17 old student reported that he build a reactor in the basement of his parents and scientists have found his reports true.
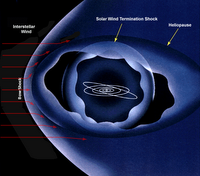
Ulysses is a joint ESA/NASA mission studying the interplanetary medium and solar wind in the inner heliosphere, beyond the Sun's equator, for the first time.
The heliosphere is the immense magnetic bubble containing our solar system, solar wind, and the entire solar magnetic field. It extends well beyond the orbit of Pluto. While the density of particles in the heliosphere is very low (it's a much better vacuum than is created in a laboratory), it is full of particles of interest to heliospheric scientists.
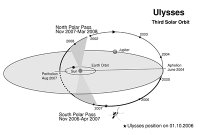
 The spacecraft's high-inclination orbit around the Sun took it over the solar south pole in 1994 and then the north pole in 1995. Ulysses then made a second southern solar pass above 70 deg latitude during September 2000 to January 2001, and a similar northern pass during September to December 2001. On 17 November 2006, the spacecraft started its third passage over the Sun's south pole.
The spacecraft's high-inclination orbit around the Sun took it over the solar south pole in 1994 and then the north pole in 1995. Ulysses then made a second southern solar pass above 70 deg latitude during September 2000 to January 2001, and a similar northern pass during September to December 2001. On 17 November 2006, the spacecraft started its third passage over the Sun's south pole.
 Ulysses' high-gain antenna points continuously towards Earth, returning data for 8 h every day as it investigates the Sun's domain.
Ulysses' high-gain antenna points continuously towards Earth, returning data for 8 h every day as it investigates the Sun's domain.
Dynamic scripting for agile application development
PHP, the open source general-purpose scripting language often used for Web development, is a popular student on campus—especially corporate campuses. According to independent research firm Netcraft, PHP is used by more than 40 percent of the Web applications market, and more than 22 million Web sites have been built with it. So what's behind this growing popularity? Let's take a closer look, starting with PHP's beginnings.
Danish computer scientist Rasmus Lerdorf created Personal Home Page/Forms Interpreter (PHP/FI), a set of Perl scripts to track access of his online résumé, in 1995. PHP/FI had some of the basic functionality of today's PHP, including Perl-like variables, automatic form variable interpretation, and HTML-embedded syntax similar to Perl's, but it was simpler and less powerful. A later, larger C implementation of PHP Tools could communicate with databases.
"Today PHP is a recursive acronym for PHP Hypertext Processor," explains Richard Rendell, product development director at Oracle. "It's come a long way in the past decade and is a powerful language for server-side scripting. PHP is a viable alternative to ASP [Active Server Pages] and JSP [JavaServer Pages]."
Rendell adds that before PHP, Web scripting was done mostly in Perl. "For a novice, Perl has a very challenging syntax and can be obtuse," says Rendell. "Perl is a powerful language, but it's not easy for people to learn—it wasn't written from the ground up to work with the internet. The internet needed a simple and highly productive scripting language, and that's where PHP came in."
Putting PHP to Work
Most developers today use PHP in Web applications from the simplest guest book or blog to shopping carts, content management systems, and other complex applications. PHP scripts are used for server-side scripting, command-line scripting, and desktop applications. With PHP server-side scripting, developers can do almost anything—generate dynamic page content, collect forms data, handle cookies—and more.
"As the PHP language has matured, its power has evolved. You can do more things with it, and we've started to see the beginning of enterprise PHP applications. These include CRM products such as SugarCRM; collaboration suites such as eGroupWare; and content management systems such as Mambo, PostNuke, and many others," says Rendell. "We're seeing PHP in an enormous number of areas, because anything you can do on the internet you can do in PHP. It's used to deliver most of the front-end, browser-centric applications on the Web today."
PHP runs on most operating systems, including Linux, UNIX, Microsoft Windows, Mac OS X, and others, and it supports most Web servers, including Apache, Zeus Web Server, lighttpd, and Microsoft Internet Information Server. In addition to HTML, PHP can output images, Adobe Acrobat files, Macromedia Flash, XML, and more—all of which can be autogenerated. There are many PHP extension libraries that perform common functions, and there are communities that support PHP libraries, including the PHP Extension and Application Repository, which provides, maintains, and distributes a structured library of common function and other code, and the PHP Extension Community Library, which offers C extensions that expand PHP's core functionality.
"The dynamically-typed-language approach PHP offers is gaining momentum for agile development," adds Rendell. "PHP is ideal for getting Web sites up and running very quickly and is now extending into complex Web applications."
For example, Rendell cites the million lines of PHP code running against an Oracle database at Trader Electronic Media, which operates AutoMart.com, the internet's largest dealer-only automotive Web site. AutoMart.com uses PHP and Oracle to deploy this high-volume site—a scalable, secure, open source Web site that posts more than half a million ads and manages more than 2.5 million visitors each month.
PHP, Java, and Ajax
PHP's streamlined functionality is essential for organizations with limited development resources and intense deadline pressure. With PHP even nondevelopers can be productive in days, and developers with experience in C, C++, or Java can be productive in hours.
"Often there's a great amount of engineering that goes into building a Java application when a simpler PHP Web application might suffice," says Rendell. "The J2EE framework, for example, is something the PHP community tends to hold up as a fairly complex entity."
PHP's basic tenet, explains Rendell, is to be fast and easy to use, so developers can be very productive very quickly. This agile approach lends itself to the front end of more-complex Java applications. "JSP is just one language that accesses Java objects. PHP also integrates with Java, so it can be used as the scripting language for activating Java logic, just like JSP," explains Rendell. "We're seeing an increased amount of integration between PHP and Java, where a Java application is running on the back end and PHP is running on the front end."
Ajax (Asynchronous JavaScript and XML) is a development technique that combines JavaScript, XML, and other technologies to create interactive Web applications. The combined Ajax technologies add functionality to the front-end development of Web applications.
"Ajax is a browser-centric solution in which JavaScript is used with XML to prevent the browser from having to refresh the entire page when data changes, such as at the database or when pieces on the page need to be refreshed," says Rendell. "You can use Ajax on the front end with Java, or you can use Ajax similarly with PHP. There are already frameworks for PHP that enable you to use and incorporate Ajax."
Zend Core for Oracle Database
Not long ago, installing PHP with Oracle was a time-consuming process. Developers had to download a variety of components—PHP, Apache, Linux, and the Oracle extension for PHP—install an Oracle client, and configure everything, which often led to integration issues.
To address the challenges facing developers who need to build their own multicomponent stack, Oracle offers Zend Core for Oracle, a free, integrated tool designed to help developers build and deploy database-driven PHP-based applications for Oracle. A fully tested and supported PHP 5 distribution, Zend Core for Oracle includes tight integration with Oracle Database 10g client libraries. It also contains a refactored OCI8 driver with substantial code improvements and new connection controls.
"Zend Core for Oracle is a prebuilt binary of all those technologies," says Rendell. "For example, on Linux we have all of the Linux parts of the stack, including PHP and the Oracle Instant Client, built into a single distribution configured on the platform through a basic Web browser interface. You're up and running in minutes."
PHP 5, PHP 6, and Beyond
"The overall direction for PHP as it matures is to make its way into more enterprise-level applications as organizations take advantage of the agility and ease of learning that PHP affords," says Rendell. "With PHP 5, development organizations are able to create more-powerful applications in much less time, which reduces costs."
PHP 5 includes features to address enterprise needs, including an updated Zend engine, extended XML, Web services, and enhanced database support. The engine, a core component that powers PHP, includes more than a dozen object-oriented development features that allow organizations to create maintainable component-based enterprise applications. XML support includes general XML extensions written to use the Gnome Project's XML and XSLT libraries. A new SimpleXML feature enables developers to manipulate XML files as if they were PHP objects. PHP 5 also includes a SOAP module, allowing interoperability with Web services, and extended database support that takes advantage of the new engine's object-oriented extensibility.
As with any student on campus, popularity ebbs and flows, and successful students—and standards—must evolve and grow if they're to retain that popularity. So what can developers expect in PHP 6?
"Frameworks are being built at the moment, and there are PHP community projects under way," says Rendell. "The language will be adopting features such as Unicode support, which is planned for PHP 6. This is an important part of becoming an enterprise-grade language, and we see PHP establishing itself as one of the three main pillars of technology for building Web applications: Java, .NET, and PHP."
The article is orgiganly done by Rich Schwerin for Oracle Magazine, Rich Schwerin is a product marketing manager with Oracle Technology Marketing. The article is also republished on terminalcult.org
Why this post? First of all, because this is my weblog and I can post whatever I like and because I really like the Dropkick Murphys and because I really like this song. As a fan I think I can pollute this weblog with some music.
"Tessie" is the title of a Broadway song, as well as another song about how the singing of "Tessie" helped the Boston Red Sox win the first World Series in 1903.
In 2004, the Boston-area punk rock group Dropkick Murphys recorded a cover of "Tessie," released on a five-cut CD single of the same name (and also featured as the bonus track on their June, 2005 release, "The Warrior's Code"). The Murphys said it was their intent to "bring back the spirit of the Rooters and to put the Red Sox back on top." Oddly enough, the goal of the Murphys was realized when later that year the Boston Red Sox won their first World Series in 86 years.
The second "Tessie" — which featured backing vocals from Red Sox players Johnny Damon, Bronson Arroyo, and Lenny DiNardo, Red Sox Vice President of Public Affairs Dr. Charles Steinberg; and Boston Herald sportswriter Jeff Horrigan (who co-wrote the new lyrics with the Murphys) — has become a theme song for the Red Sox and tells the story of how the Royal Rooters stormed the park one time when they found the game was already sold out:
"Tessie"
Tessie is the Royal Rooters rally cry
Tessie is the tune they always sung
Tessie echoed April through October nights
After serenading Stahl, Dinneen and Young
Tessie is a maiden with a sparkling eye
Tessie is a maiden with a love
She doesn't know the meaning of her sight
She's got a comment full of love
And sometimes when the game is on the line
Tessie always carried them away
Up the road from "Third Base" to Huntington
The boys will always sing and sway
Two! Three! Four!
Tessie, "Nuf Ced" McGreevey shouted
We're not here to mess around
Boston, you know we love you madly
Hear the crowd roar to your sound
Don't blame us if we ever doubt you
You know we couldn't live without you
Tessie, you are the only only only
The Rooters showed up at the grounds one day
They found their seats had all been sold
McGreevey led the charge into the park
Stormed the gates and put the game on hold
The Rooters gave the other team a dreadful fright
Boston's tenth man could not be wrong
Up from "Third Base" to Huntington
They'd sing another victory song
Two! Three! Four!
Tessie, "Nuf Ced" McGreevey shouted
We're not here to mess around
Boston, you know we love you madly
Hear the crowd roar to your sound
Don't blame us if we ever doubt you
You know we couldn't live without you
Tessie, you are the only only only
The Rooters gave the other team a dreadful fright
Boston's tenth man could not be wrong
Up from "Third Base" to Huntington
They'd sing another victory song
Two! Three! Four!
Tessie, "Nuf Ced" McGreevey shouted
We're not here to mess around
Boston, you know we love you madly
Hear the crowd roar to your sound
Don't blame us if we ever doubt you
You know we couldn't live without you
Tessie, you are the only only only
Don't blame us if we ever doubt you
You know we couldn't live without you
Boston, you are the only only only
Don't blame us if we ever doubt you
You know we couldn't live without you
Red Sox, you are the only only only
An orbiting NASA spacecraft just starting to study Mars with six science instruments has successfully tested another key part of its payload, a versatile radio for relaying communications with robots on the surface of Mars.
During its first relay test since reaching Mars in March, the Mars Reconnaissance Orbiter used this radio payload, called Electra, in a two-way link with NASA's Mars Exploration Rover Spirit. The orbiter has dual roles as a science mission and a telecommunications satellite. It will support communications between Earth and future Mars surface missions, such as the 2007 Phoenix Mars Lander and 2009 Mars Science Laboratory.
"The successful test establishes Mars Reconnaissance Orbiter as a key element of our Mars telecommunications infrastructure," said Chad Edwards, chief telecommunications engineer of the Mars Network Office at NASA's Jet Propulsion Laboratory, Pasadena, Calif. "With its Electra relay payload, this orbiter will play a critical role in providing robust, high-bandwidth communications links for our future landers later this decade and into the next. It will increase the science return from these missions and enhance our virtual presence on the Martian surface."
JPL's Jim Graf, project manager for Mars Reconnaissance Orbiter, said, "Our primary science phase started Nov. 7, and this successful Electra test shows we're also in good shape for the following phase, the relay phase of the mission. Both phases will make good use of our orbiter's capability for sending data to Earth at up to 10 times the rate of any previous Mars mission."
Using Mars orbiters as radio relays to increase data return from rovers and other landers reduces the mass and power the surface spacecraft need for communications. To build the relay network cost-effectively, NASA includes a relay communications payload on each of its science orbiters.
Mars Global Surveyor, at Mars since 1997, and Mars Odyssey, there since 2001, established a relay capacity that the twin rovers Spirit and Opportunity have used extensively since their 2004 landings. More than 96 percent of the data returned from the rovers has come to Earth via energy-efficient relay through those two orbiters, at much higher data rates than the rovers can achieve on their direct links to Earth.
The Electra package on Mars Reconnaissance Orbiter, like the relay radios on Global Surveyor and Odyssey, uses an ultra-high-frequency (UHF) portion of the radio spectrum. In addition to its relay function, Electra can also be used by surface missions, or by future spacecraft approaching Mars, to determine their positions with precision and to synchronize their clocks.
During last week's tests, Electra initiated a relay session by hailing the Spirit rover. Spirit responded with its own relay radio, and the two spacecraft established a link at 8 kilobits per second on the forward link from Mars Reconnaissance Orbiter to Spirit and 128 kilobits per second from Spirit back to the orbiter. Both radios used a communications standard called the Proximity-1 Space Link Protocol, established by the international Consultative Committee for Space Data Systems for ensuring compatible and gap-free communications on such relay links.
During the four-minute session, the orbiter delivered five commands to the rover, and the rover sent up 30 megabits of information, which the orbiter subsequently transmitted to Earth for delivery to the rover's operations team at JPL.
Nearly all of the signal-processing capabilities of Electra can be reprogrammed in flight, giving it more flexibility than earlier spacecraft relay radios.
"Electra is NASA's first software-defined radio sent to deep space," said JPL's Tom Jedrey, manager for the Electra payload. "From the ground, we can change the fundamentals of its signal processing whenever that is helpful. This means it will be able to accommodate new communication protocols and signal-processing methods over the course of the Mars Reconnaissance Orbiter's operational life."
Additional information about Mars Reconnaissance Orbiter is available online at http://www.nasa.gov/mro . The mission is managed by JPL, a division of the California Institute of Technology in Pasadena, for the NASA Science Mission Directorate, Washington. Lockheed Martin Space Systems, Denver, is the prime contractor for the project and built the spacecraft.
It's called Apophis. It's 390m wide. And it could hit Earth in 31 years time. A meteorite on a collision course with planet earth. When it hits the earth atmosphere and moments later the surface it will make a hell of show and that is a very big understatement.
In Egyptian myth, Apophis was the ancient spirit of evil and destruction, a demon that was determined to plunge the world into eternal darkness. And this Apophis could very well do the same thing. Nasa has estimated that an impact from Apophis, which has an outside chance of hitting the Earth in 2036, would release more than 100,000 times the energy released in the nuclear blast over Hiroshima. Thousands of square kilometres would be directly affected by the blast but the whole of the Earth would see the effects of the dust released into the atmosphere.
And, scientists insist, there is actually very little time left to decide. At a recent meeting of experts in near-Earth objects (NEOs) in London, scientists said it could take decades to design, test and build the required technology to deflect the asteroid. Monica Grady, an expert in meteorites at the Open University, said: "It's a question of when, not if, a near Earth object collides with Earth. Many of the smaller objects break up when they reach the Earth's atmosphere and have no impact. However, a NEO larger than 1km [wide] will collide with Earth every few hundred thousand years and a NEO larger than 6km, which could cause mass extinction, will collide with Earth every hundred million years. We are overdue for a big one."
Apophis had been intermittently tracked since its discovery in June last year but, in December, it started causing serious concern. Projecting the orbit of the asteroid into the future, astronomers had calculated that the odds of it hitting the Earth in 2029 were alarming. As more observations came in, the odds got higher.
Having more than 20 years warning of potential impact might seem plenty of time. But, at last week's meeting, Andrea Carusi, president of the Spaceguard Foundation, said that the time for governments to make decisions on what to do was now, to give scientists time to prepare mitigation missions. At the peak of concern, Apophis asteroid was placed at four out of 10 on the Torino scale - a measure of the threat posed by an NEO where 10 is a certain collision which could cause a global catastrophe. This was the highest of any asteroid in recorded history and it had a 1 in 37 chance of hitting the Earth. The threat of a collision in 2029 was eventually ruled out at the end of last year.
Alan Fitzsimmons, an astronomer from Queen's University Belfast, said: "When it does pass close to us on April 13 2029, the Earth will deflect it and change its orbit. There's a small possibility that if it passes through a particular point in space, the so-called keyhole, ... the Earth's gravity will change things so that when it comes back around again in 2036, it will collide with us." The chance of Apophis passing through the keyhole, a 600-metre patch of space, is 1 in 5,500 based on current information.
There are no shortage of ideas on how to deflect asteroids. The Advanced Concepts Team at the European Space Agency have led the effort in designing a range of satellites and rockets to nudge asteroids on a collision course for Earth into a different orbit.
No technology has been left unconsidered, even potentially dangerous ideas such as nuclear powered spacecraft. "The advantage of nuclear propulsion is a lot of power," said Prof Fitzsimmons. "The negative thing is that ... we haven't done it yet. Whereas with solar electric propulsion, there are several spacecraft now that do use this technology so we're fairly confident it would work."
The favoured method is also potentially the easiest - throwing a spacecraft at an asteroid to change its direction. Esa plans to test this idea with its Don Quixote mission, where two satellites will be sent to an asteroid. One of them, Hidalgo, will collide with the asteroid at high speed while the other, Sancho, will measure the change in the object's orbit. Decisions on the actual design of these probes will be made in the coming months, with launch expected some time in the next decade. One idea that seems to have no support from astronomers is the use of explosives.
Prof Fitzsimmons. "If you explode too close to impact, perhaps you'll get hit by several fragments rather than one, so you spread out the area of damage."
In September, scientists at Strathclyde and Glasgow universities began computer simulations to work out the feasibility of changing the directions of asteroids on a collision course for Earth. In spring next year, there will be another opportunity for radar observations of Apophis that will help astronomers work out possible future orbits of the asteroid more accurately.
If, at that stage, they cannot rule out an impact with Earth in 2036, the next chance to make better observations will not be until 2013. Nasa has argued that a final decision on what to do about Apophis will have to be made at that stage.
"It may be a decision in 2013 whether or not to go ahead with a full-blown mitigation mission, but we need to start planning it before 2013," said Prof Fitzsimmons. In 2029, astronomers will know for sure if Apophis will pose a threat in 2036. If the worst-case scenarios turn out to be true and the Earth is not prepared, it will be too late. "If we wait until 2029, it would seem unlikely that you'd be able to do anything about 2036," said Mr Yates.
In his CRYPTO-GRAM of November 15, 2006 Bruce Schneier, Founder and CTO Counterpane Internet Security, Inc is discussing Architecture and Security. Please find the article below.
You've seen them: those large concrete blocks in front of skyscrapers, monuments and government buildings, designed to protect against car and truck bombs. They sprang up like weeds in the months after 9/11, but the idea is much older. The prettier ones doubled as planters; the uglier ones just stood there.
Form follows function. From medieval castles to modern airports, security concerns have always influenced architecture. Castles appeared during the reign of King Stephen of England because they were the best way to defend the land and there wasn't a strong king to put any limits on castle-building. But castle design changed over the centuries in response to both innovations in warfare and politics, from motte-and-bailey to concentric design in the late medieval period to entirely decorative castles in the 19th century.
These changes were expensive. The problem is that architecture tends toward permanence, while security threats change much faster. Something that seemed a good idea when a building was designed might make little sense a century -- or even a decade -- later. But by then it's hard to undo those architectural decisions.
When Syracuse University built a new campus in the mid-1970s, the student protests of the late 1960s were fresh on everybody's mind. So the architects designed a college without the open greens of traditional college campuses. It's now 30 years later, but Syracuse University is stuck defending itself against an obsolete threat.
Similarly, hotel entries in Montreal were elevated above street level in the 1970s, in response to security worries about Quebecois separatists. Today the threat is gone, but those older hotels continue to be maddeningly difficult to navigate.
Also in the 1970s, the Israeli consulate in New York built a unique security system: a two-door vestibule that allowed guards to identify visitors and control building access. Now this kind of entryway is widespread, and buildings with it will remain unwelcoming long after the threat is gone.
The same thing can be seen in cyberspace as well. In his book, "Code and Other Laws of Cyberspace," Lawrence Lessig describes how decisions about technological infrastructure -- the architecture of the internet -- become embedded and then impracticable to change. Whether it's technologies to prevent file copying, limit anonymity, record our digital habits for later investigation or reduce interoperability and strengthen monopoly positions, once technologies based on these security concerns become standard it will take decades to undo them.
It's dangerously shortsighted to make architectural decisions based on the threat of the moment without regard to the long-term consequences of those decisions.
Concrete building barriers are an exception: They're removable. They started appearing in Washington, D.C., in 1983, after the truck bombing of the Marines barracks in Beirut. After 9/11, they were a sort of bizarre status symbol: They proved your building was important enough to deserve protection. In New York City alone, more than 50 buildings were protected in this fashion.
Today, they're slowly coming down. Studies have found they impede traffic flow, turn into giant ashtrays and can pose a security risk by becoming flying shrapnel if exploded.
We should be thankful they can be removed, and did not end up as permanent aspects of our cities' architecture. We won't be so lucky with some of the design decisions we're seeing about internet architecture.
This essay originally appeared in Wired.com.
Concrete barriers coming down in New York.
Activism-restricting architecture at the University of Texas.
Commentary from the Architectures of Control in Design Blog.
Samsung has partnered with Korea university and developed the machine-gun equipped robotic sentry. It is equipped with two cameras with zooming capabilities one for day time and one for infrared night vision. It has a sophisticated pattern recognition which can detect the difference between humans and trees, and a 5.5mm machine-gun. The robot also has a speaker to warn the intruder to surrender or get a perfect headshot. The robots will go on sale by 2007 for $ 200,000 and will be deployed on the border between North and South Korea.
This news reminds me of the rules of robotics which are set by Isaac Asimov Even do Asimov was a writer of SF books the things he wrote about ethics for robots are accepted by the majority of the scientific community building robots.
- A robot may not injure a human being or, through inaction, allow a human being to come to harm.
- A robot must obey orders given it by human beings except where such orders would conflict with the First Law.
- A robot must protect its own existence as long as such protection does not conflict with the First or Second Law.
The US army also already has some armed robots and this also is considered against moral standards by a large number of leading researchers. As already stated Asimov was a novel writer however the things he wrote on this subject are a good and clear guideline, which should be respected by researchers and companies in my opinion.
NASA, Notional Aeronautics and Space Administration, can be considered as one of the largest US government funded research institutes. As all research institutes at this moment there is a large amount of open-source software involved. A large number of there researchers are using Linux on there computers and a large number of there servers are running on Linux.
Also a lot of the researchers at NASA are giving back open-source software and enhancements to the open-source community. Also they have some projects running completely devoted to open-source. For example the “World Wind” project which is a open-source project. This project is licensed under “NASA OPEN SOURCE AGREEMENT VERSION 1.3”
The big advantage of open-source at NASA is that the community can tap into the knowledge of NASA and there are some very nice projects you can download and participate in. Some good places to take a look are for example the “Ames Research Center” or the “Goddard Space Flight Center, Office of Technology Transfer”. Also a good place to take a first look is at this location.
Here you can find links to projects like:
ACE: aCe (Architecture Adaptive Computing Environment) is a project to develop a programming environment that can be supported on all computing architectures.
ECHO:The EOS ClearingHOuse (ECHO) is an enabling framework being built by NASA's Earth Science Data and Information System (ESDIS) Project to allow different data systems and services to work together. ECHO is an open system based on Extensible Markup Language (XML) and Web Service technologies; its Application Program Interfaces (APIs) are published for use by the science community to exchange data, information, and services.
OSAL: The Operating System Abstraction Layer is a small software library that isolates embedded system software from a real time operating system. The project includes an Operating System Application Program Interface (API), a Hardware Abstraction Layer API, implementations for several real time and desktop operating systems, and a project build system.
Livingstone2: Livingstone2 is a reusable artificial intelligence (AI) software system designed to assist spacecraft, life support systems, chemical plants or other complex systems in operating robustly with minimal human supervision, even in the face of hardware failures or unexpected events.
CODE: CODE is a software framework for control and observation in distributed environments. This framework enables the observation of distributed resources, services, and applications. Observations are made by modular components called sensors, the information observed is encapsulated as events, and these events are transmitted from where they are produced to whoever wants to consume them using an event management framework. Further, the CODE framework allows people or agents to control a distributed system by allowing them to take actions on remote systems using modular components called actors.
Surfer: Surfer is a general-purpose framework for selecting and ranking grid resources based on user constraints and preferences. Surfer has no built-in bias towards any job model or selection policy, thus is suitable for inclusion in any grid environment by adding information providers knowledgeable about that environment. Information is pulled from these providers as needed allowing Surfer to efficiently handle large and complex information sources unsuitable for push-based models. Surfer has been implemented as an OGSI-compliant grid service that can also be embedded directly into Java applications through its APIs or into non-Java applications through its XML-based command-line interface.
JavaGenes: JavaGenes is a fairly general purpose evolutionary software system written in Java. It implements several versions of the genetic algorithm, simulated annealing, stochastic hill climbing and other search techniques. JavaGenes has been used to evolve molecules, atomic force field parameters, digital circuits, Earth Observing Satellite schedules, and antennas. The digital circuit searches didn't work very well and the code isn't here. The antenna code is not, and may never be, available for open source distribution. Compared to version 0.7.28, this version includes the molecule evolution code and a number of other improvements.
The man command in UNIX and Linux environments give you a manual page about a specific command while you are working in a terminal environment. This can be convenient while working on the terminal however from time to time you might want to explore some commands when you do not have access to a command shell.
Panagiotis Christias created a shell-sed-awk script which converts on the fly the output of the "man" command to HTML named Man-cgi. The university of Alabama installed this on a Sun Solaris. On my website terminalcult.org I created a interface to the Sun machine at UA and parsed the HTML output into the format of the terminalcult website. So now it is possible to explorer the Sun Solaris commands from my website.
 I also created a raw index of some of the most used commands. You can find some links below.
I also created a raw index of some of the most used commands. You can find some links below.
- accept – accept or reject print requests
- acct – overview of accounting and miscellaneous accounting commands
- acctadm – configure extended accounting facility
- acctcms – command summary from process accounting records
- acctcon – connect-time accounting
- acctcon1 – connect-time accounting
- acctcon2 – connect-time accounting
- acctdisk – overview of accounting and miscellaneous accounting commands
- acctdusg – overview of accounting and miscellaneous accounting commands
- acctmerg – merge or add total accounting files
- accton – overview of accounting and miscellaneous accounting commands
- acctprc – process accounting
- acctprc1 – process accounting
- acctprc2 – process accounting
- acctsh – shell procedures for accounting
- acctwtmp – overview of accounting and miscellaneous accounting commands
- adbgen – generate adb script
- add_drv – add a new device driver to the system
- add_install_client – scripts used to install the Solaris software
- add_to_install_server – scripts used to install the Solaris software
- addbadsec – map out defective disk blocks
- afbconfig – configure the AFB Graphics Accelerator
- aliasadm – manipulate the NIS+ aliases map
- answerbook2_admin – bring up AnswerBook2 administration tool GUI
- apache – Apache hypertext transfer protocol server overview
- arp – address resolution display and control
- aset – monitors or restricts accesses to system files and directories
- aset.restore – restores system files to their content before ASET is installed
- audit – control the behavior of the audit daemon
- audit_startup – audit subsystem initialization script
- audit_warn – audit daemon warning script
- auditconfig – configure auditing
- auditd – audit daemon
- auditreduce – merge and select audit records from audit trail files
- auditstat – display kernel audit statistics
- automount – install automatic mount points
- automountd – autofs mount/unmount daemon
- autopush – configures lists of automatically pushed STREAMS modules
- bart – basic audit reporting tool
- bdconfig – configures the bd (buttons and dials) stream
- boot – start the system kernel or a standalone program
- bootadm – manage bootability of GRUB-enabled operating system
- bootconfchk – verify the integrity of a network boot configuration file
- bootparamd – boot parameter server
- bsmconv – enable or disable the Basic Security Module (BSM) on Solaris
- bsmrecord – display Solaris audit record formats
- bsmunconv – enable or disable the Basic Security Module (BSM) on Solaris
- busstat – report bus-related performance statistics
- cachefsd – CacheFS daemon
- cachefslog – Cache File System logging
- cachefspack – pack files and file systems in the cache
- cachefsstat – Cache File System statistics
- cachefswssize – determine working set size for cachefs
- captoinfo – convert a termcap description into a terminfo description
- catman – create the formatted files for the reference manual
- cfgadm – configuration administration
- cfgadm_ac – EXX00 memory system administration
- cfgadm_fp – driver specific commands for cfgadm
- cfgadm_ib – InfiniBand hardware specific commands for cfgadm
- cfgadm_pci – PCI, CompactPCI, and PCI Express Hotplug hardware specific commands for cfgadm
- cfgadm_sata – SATA hardware specific commands specific commands for cfgadm
- cfgadm_sbd – cfgadm commands for system board administration
- cfgadm_scsi – SCSI hardware specific commands for cfgadm
- cfgadm_sysctrl – EXX00 system board administration
- cfgadm_usb – USB hardware-specific commands for cfgadm
- cfsadmin – administer disk space used for caching file systems with the Cache File-System (CacheFS)
- chargefee – shell procedures for accounting
- chat – automated conversational exchange tool
- check – scripts used to install the Solaris software
- check-hostname – check if sendmail can determine the system's fully-qualified host name
- check-permissions – check permissions on mail rerouting files
- chroot – change root directory for a command
- cimworkshop – start the Sun WBEM CIM WorkShop application
- ckpacct – shell procedures for accounting
- clear_locks – clear locks held on behalf of an NFS client
- clinfo – display cluster information
- closewtmp – overview of accounting and miscellaneous accounting commands
- clri – clear inode
- comsat – biff server
- consadm – select or display devices used as auxiliary console devices
- conv_lp – convert LP configuration
- conv_lpd – convert LPD configuration
- coreadm – core file administration
- cpustat – monitor system behavior using CPU performance counters
- cron – clock daemon
- cryptoadm – cryptographic framework administration
- cvcd – virtual console daemon
- datadm – maintain DAT static registry file
- dcopy – clear inode
- dcs – domain configuration server
- dd – convert and copy a file
- devattr – display device attributes
- devfree – release devices from exclusive use
- devfsadm – administration command for /dev
- devfsadmd – administration command for /dev
- devinfo – print device specific information
- devlinks – adds /dev entries for miscellaneous devices and pseudo-devices
- devnm – device name
- devreserv – reserve devices for exclusive use
- df – displays number of free disk blocks and free files
- df_ufs – report free disk space on ufs file systems
- dfmounts – display mounted resource information
- dfmounts_nfs – display mounted NFS resource information
- dfshares – list available resources from remote or local systems
- dfshares_nfs – list available NFS resources from remote systems
- dhcpagent – Dynamic Host Configuration Protocol (DHCP) client daemon
- dhcpconfig – DHCP service configuration utility
- dhcpmgr – graphical interface for managing DHCP service
- dhtadm – DHCP configuration table management utility
- dig – DNS lookup utility
- directoryserver – front end for the Directory Server (DS)
- disks – creates /dev entries for hard disks attached to the system
- diskscan – perform surface analysis
- dispadmin – process scheduler administration
- dladm – configure data-link interfaces
- dmesg – collect system diagnostic messages to form error log
- dmi_cmd – DMI command line interface utility
- dmiget – DMI command line retrieval utility
- dminfo – report information about a device entry in a device maps file
- dmispd – Sun Solstice Enterprise DMI Service Provider
- dnssec-keygen – DNSSEC key generation tool
- dnssec-makekeyset – DNSSEC zone signing tool
- dnssec-signkey – DNSSEC key set signing tool
- dnssec-signzone – DNSSEC zone signing tool
- dodisk – shell procedures for accounting
- domainname – set or display name of the current domain
- drvconfig – apply permission and ownership changes to devices
- dsvclockd – DHCP service lock daemon
- dtrace – DTrace dynamic tracing compiler and tracing utility
- dumpadm – configure operating system crash dump
- editmap – query and edit single records in database maps for sendmail
- edquota – edit user quotas for ufs file system
- eeprom – EEPROM display and load utility
- efdaemon – embedded FCode interpreter daemon
- embedded_su – allow an application to prompt for credentials and execute commands as the super user or another user
- etrn – start mail queue run
- fbconfig – Frame Buffer configuration utility
- fcinfo – Fibre Channel HBA Port Command Line Interface
- fdetach – detach a name from a STREAMS-based file descriptor
- fdisk – create or modify fixed disk partition table
- ff – list file names and statistics for a file system
- ff_ufs – list file names and statistics for a ufs file system
- ffbconfig – configure the FFB Graphics Accelerator
- fingerd – remote user information server
- flar – administer flash archives
- flarcreate – create a flash archive from a master system
- fmadm – fault management configuration tool
- fmd – fault manager daemon
- fmdump – fault management log viewer
- fmstat – report fault management module statistics
- fmthard – populate label on hard disks
- format – disk partitioning and maintenance utility
- fruadm – prints and updates customer data associated with FRUs
- fsck – check and repair file systems
- fsck_cachefs – check integrity of data cached with CacheFS
- fsck_pcfs – file system consistency check and interactive repair
- fsck_udfs – file system consistency check and interactive repair
- fsck_ufs – file system consistency check and interactive repair
- fsdb – file system debugger
- fsdb_udfs – udfs file system debugger
- fsdb_ufs – ufs file system debugger
- fsirand – install random inode generation numbers
- fssnap – create temporary snapshots of a file system
- fssnap_ufs – create a temporary snapshot of a UFS file system
- fstyp – determine file system type
- ftpaddhost – set up a virtual FTP host
- ftpconfig – set up anonymous FTP
- ftpd – File Transfer Protocol Server
- ftprestart – restart previously shutdown FTP Servers
- ftpshut – close down the FTP Servers at a given time
- fuser – identify users of files and devices
- fwtmp – manipulate connect accounting records
- getdev – lists devices based on criteria
- getdevpolicy – inspect the system's device policy
- getdgrp – lists device groups which contain devices that match criteria
- getent – get entries from administrative database
- gettable – get DoD Internet format host table from a host
- getty – set terminal type, modes, speed, and line discipline
- getvol – verifies device accessibility
- GFXconfig – configure the PGX32 (Raptor GFX) Graphics Accelerator
- gkadmin – Kerberos database administration GUI, SEAM Administration Tool
- groupadd – add (create) a new group definition on the system
- groupdel – delete a group definition from the system
- groupmod – modify a group definition on the system
- growfs – non-destructively expand a UFS file system
- grpck – password/group file checkers
- gsscred – add, remove and list gsscred table entries
- gssd – generates and validates GSS-API tokens for kernel RPC
- halt – stop the processor
- host – DNS lookup utility
- hostconfig – configure a system's host parameters
- htable – convert DoD Internet format host table
- ickey – install a client key for WAN boot
- id – return user identity
- idsconfig – prepare an iPlanet Directory Server (iDS) to be populated with data and serve LDAP clients
- if_mpadm – change operational status of interfaces within a multipathing group
- ifconfig – configure network interface parameters
- ifparse – parse ifconfig command line
- ikeadm – manipulate Internet Key Exchange (IKE) parameters and state
- ikecert – manipulates the machine's on-filesystem public-key certificate databases
- imqadmin – launch the Message Queue administration console
- imqbrokerd – start a Message Queue broker instance
- imqcmd – manage Message Queue brokers
- imqdbmgr – manage a plugged-in JDBC-compliant Message Queue data store
- imqkeytool – generate a self-signed certificate for secure communication
- imqobjmgr – manage Message Queue administered objects
- imqusermgr – command utility for managing a Message Queue user repository
- in.chargend – UDP or TCP character generator service daemon
- in.comsat – biff server
- in.daytimed – UDP or TCP daytime protocol service daemon
- in.dhcpd – Dynamic Host Configuration Protocol server
- in.discardd – UDP or TCP discard protocol service
- in.echod – UDP or TCP echo protocol service daemon
- in.fingerd – remote user information server
- in.ftpd – File Transfer Protocol Server
- in.iked – daemon for the Internet Key Exchange (IKE)
- in.lpd – BSD print protocol adaptor
- in.mpathd – daemon for network adapter (NIC) failure detection, recovery, automatic failover and failback
- in.named – Internet domain name server
- in.ndpd – daemon for IPv6 autoconfiguration
- in.rarpd – DARPA Reverse Address Resolution Protocol server
- in.rdisc – network router discovery daemon
- in.rexecd – remote execution server
- in.ripngd – network routing daemon for IPv6
- in.rlogind – remote login server
- in.routed – network routing daemon
- in.rshd – remote shell server
- in.rwhod – system status server
- in.talkd – server for talk program
- in.telnetd – DARPA TELNET protocol server
- in.tftpd – Internet Trivial File Transfer Protocol server
- in.timed – UDP or TCP time protocol service daemon
- in.tnamed – DARPA trivial name server
- in.uucpd – UUCP server
- inetadm – observe or configure inetd-controlled services
- inetconv – convert inetd.conf entries into smf service manifests, import them into smf repository
- inetd – Solaris Management Facility delegated restarter for inet services
- infocmp – compare or print out terminfo descriptions
- init – process control initialization
- init.sma – start and stop the snmpd daemon
- init.wbem – start and stop the CIM Boot Manager
- inityp2l – create NIS (YP) to LDAP configuration files
- install – install commands
- install_scripts – scripts used to install the Solaris software
- installboot – install bootblocks in a disk partition
- installer – Solaris Web Start installer utility
- installf – add a file to the software installation database
- installgrub – install GRUB in a disk partition or a floppy
- install-solaris – install the Solaris operating system
- intrstat – report interrupt statistics
- iostat – report I/O statistics
- ipaddrsel – configure IPv6 default address selection
- ipf – alter packet filtering lists for IP packet input and output
- ipfs – saves and restores information for NAT and state tables
- ipfstat – reports on packet filter statistics and filter list
- ipmon – monitors /dev/ipl for logged packets
- ipnat – user interface to the NAT subsystem
- ippool – user interface to the IP Filter pools
- ipqosconf – configure the IPQoS facility
- ipsecalgs – configure the IPsec protocols and algorithms table
- ipsecconf – configure system wide IPsec policy
- ipseckey – manually manipulate an IPsec Security Association Database (SADB)
- iscsiadm – enable management of iSCSI initiators
- kadb – a kernel debugger
- kadmin – Kerberos database administration program
- kadmin.local – Kerberos database administration program
- kadmind – Kerberos administration daemon
- kcfd – kernel-level cryptographic framework daemon
- kclient – set up a machine as a Kerberos client
- kdb5_util – Kerberos Database maintenance utility
- kdmconfig – configure or unconfigure keyboard, display, and mouse options for OpenWindows and internationalization
- kernel – UNIX system executable file containing basic operating system services
- keyserv – server for storing private encryption keys
- killall – kill all active processes
- kprop – Kerberos database propagation program
- kpropd – Kerberos propagation daemon for slave KDCs
- kproplog – display the contents of the Kerberos principal update log
- krb5kdc – KDC daemon
- kstat – display kernel statistics
- ktkt_warnd – Kerberos warning daemon
- labelit – list or provide labels for file systems
- labelit_hsfs – provide and print labels for hsfs file systems
- labelit_udfs – provide and print labels for udf file systems
- labelit_ufs – provide and print labels for ufs file systems
- lastlogin – shell procedures for accounting
- ldap_cachemgr – LDAP daemon to manage client configuration for LDAP based Network Information Service lookups
- ldapaddent – create LDAP entries from corresponding /etc files
- ldapclient – initialize LDAP client machine or output an LDAP client profile in LDIF format
- link – link and unlink files and directories
- listdgrp – lists members of a device group
- listen – network listener daemon
- llc2_loop – loopback diagnostics to test the driver, adapter and network.
- localeadm – query and configure locales
- locator – location indicator control
- lockd – network lock daemon
- lockfs – change or report file system locks
- lockstat – report kernel lock and profiling statistics
- lofiadm – administer files available as block devices through lofi
- logadm – manage endlessly growing log files
- logins – list user and system login information
- lpadmin – configure the LP print service
- lpfilter – administer filters used with the LP print service
- lpforms – administer forms used with the LP print service
- lpget – get printing configuration
- lpmove – move print requests
- lpsched – start the LP print service
- lpset – set printing configuration in /etc/printers.conf or other supported databases
- lpshut – stop the LP print service
- lpsystem – register remote systems with the print service
- lpusers – set printing queue priorities
- lu – FMLI-based interface to Live Upgrade functions
- luactivate – activate a boot environment
- lucancel – cancel a scheduled Live Upgrade copy/create procedure
- lucompare – compare boot environments
- lucreate – create a new boot environment
- lucurr – display the name of the active boot environment
- ludelete – delete a boot environment
- ludesc – display or set boot environment description
- lufslist – list configuration of a boot environment
- lumake – populate a boot environment
- lumount – mount or unmount all file systems in a boot environment
- lurename – change the name of a boot environment
- lustatus – display status of boot environments
- luumount – mount or unmount all file systems in a boot environment
- luupgrade – installs, upgrades, and performs other functions on software on a boot environment
- luxadm – administer Sun Fire 880 storage subsystem and FC_AL devices
- m64config – configure the M64 Graphics Accelerator
- mail.local – store mail in a mailbox
- makedbm – make a dbm file, or get a text file from a dbm file
- makemap – create database maps for sendmail
- makeuuid – generate Universal Unique Identifiers
- masfcnv – SNMP configuration migration script
- mdlogd – Solaris Volume Manager daemon
- mdmonitord – daemon to monitor metadevices
- medstat – check the status of mediator hosts for a given diskset
- metaclear – delete active metadevices and hot spare pools
- metadb – create and delete replicas of the metadevice state database
- metadetach – attach or detach a metadevice
- metadevadm – update metadevice information
- metahs – manage hot spares and hot spare pools
- metaimport – imports disk sets into existing Solaris Volume Manager configurations
- metainit – configure metadevices
- metaoffline – place submirrors offline and online
- metaonline – place submirrors offline and online
- metaparam – modify parameters of metadevices
- metarecover – recover soft partition information
- metarename – rename metadevice or switch layered metadevice names
- metareplace – enable or replace components of submirrors or RAID5 metadevices
- metaroot – setup system files for root (/) metadevice
- metaset – configure disk sets
- metassist – automated volume creation utility to support Solaris Volume Manager
- metastat – display status for metadevice or hot spare pool
- metasync – handle metadevice resync during reboot
- metattach – attach or detach a metadevice
- mib2c – produces template code from MIB definitions
- mib2mof – generate MOF file(s) from input SNMP MIB file(s)
- mibiisa – Sun SNMP Agent
- mipagent – Mobile IP agent
- mipagentconfig – configure Mobility IP Agent
- mipagentstat – show Mobile IP Mobility Agent status
- mkdevalloc – Make device_allocate entries
- mkdevmaps – make device_maps entries
- mkfifo – make FIFO special file
- mkfile – create a file
- mkfs – construct a file system
- mkfs_pcfs – construct a FAT file system
- mkfs_udfs – construct a udfs file system
- mkfs_ufs – construct a UFS file system
- mknod – make a special file
- mkpwdict – maintain password-strength checking database
- modinfo – display information about loaded kernel modules
- modload – load a kernel module
- modunload – unload a module
- mofcomp – compile MOF files into CIM classes
- mofreg – register MOF classes with WBEM services
- monacct – shell procedures for accounting
- monitor – SPARC system PROM monitor
- mount – mount or unmount file systems and remote resources
- mount_cachefs – mount CacheFS file systems
- mount_hsfs – mount hsfs file systems
- mount_nfs – mount remote NFS resources
- mount_pcfs – mount pcfs file systems
- mount_tmpfs – mount tmpfs file systems
- mount_udfs – mount a udfs file system
- mount_ufs – mount ufs file systems
- mount_xmemfs – mount xmemfs file systems
- mountall – mount, unmount multiple file systems
- mountd – server for NFS mount requests and NFS access checks
- mpstat – report per-processor or per-processor-set statistics
- msgid – generate message IDs
- mvdir – move a directory
- named – Internet domain name server
- named-checkconf – named configuration file syntax checking tool
- named-checkzone – zone file validity checking tool
- ncaconfd – Solaris Network Cache and Accelerator (NCA) configuration daemon
- ncheck – generate a list of path names versus i-numbers
- ncheck_ufs – generate pathnames versus i-numbers for ufs file systems
- ndd – get and set driver configuration parameters
- netstat – show network status
- newaliases – rebuild the data base for the mail aliases file
- newfs – construct a UFS file system
- newkey – create a new Diffie-Hellman key pair in the publickey database
- nfs4cbd – NFS Version 4 callback daemon
- nfsd – NFS daemon
- nfslogd – nfs logging daemon
- nfsmapid – NFS user and group id mapping daemon
- nfsstat – NFS statistics
- nis_cachemgr – NIS+ utility to cache location information about NIS+ servers
- nisaddcred – create NIS+ credentials
- nisaddent – create NIS+ tables from corresponding /etc files or NIS maps
- nisauthconf – configure NIS+ security
- nisbackup – backup NIS+ directories
- nisclient – initialize NIS+ credentials for NIS+ principals
- nisd – NIS+ service daemon
- nisd_resolv – NIS+ service daemon
- nisinit – NIS+ client and server initialization utility
- nisldapmaptest – test NIS+ and LDAP mapping configuration files
- nislog – display the contents of the NIS+ transaction log
- nispasswdd – NIS+ password update daemon
- nisping – send ping to NIS+ servers
- nispopulate – populate the NIS+ tables in a NIS+ domain
- nisprefadm – NIS+ utility to set server preferences for NIS+ clients
- nisrestore – restore NIS+ directory backup
- nisserver – set up NIS+ servers
- nissetup – initialize a NIS+ domain
- nisshowcache – NIS+ utility to print out the contents of the shared cache file
- nisstat – report NIS+ server statistics
- nisupdkeys – update the public keys in a NIS+ directory object
- nlsadmin – network listener service administration
- nscd – name service cache daemon
- nslookup – query Internet name servers interactively
- nsupdate – Dynamic DNS update utility
- ntpdate – set the date and time by way of NTP
- ntpq – standard Network Time Protocol query program
- ntptrace – trace a chain of NTP hosts back to their master time source
- nulladm – shell procedures for accounting
- obpsym – Kernel Symbolic Debugging for OpenBoot Firmware
- ocfserv – OCF server
- parse_dynamic_clustertoc – parse clustertoc file based on dynamic entries
- passmgmt – password files management
- patchadd – apply a patch package to a system running the Solaris operating system
- patchrm – remove a Solaris patch package and restore previously saved files
- pbind – control and query bindings of processes or LWPs
- pcmciad – PCMCIA user daemon
- pfinstall – tests installation profiles
- pgxconfig – configure the PGX32 (Raptor GFX) Graphics Accelerator
- picld – PICL daemon
- ping – send ICMP (ICMP6) ECHO_REQUEST packets to network hosts
- pkgadd – transfer software packages to the system
- pkgadm – manage packaging and patching system
- pkgask – stores answers to a request script
- pkgchk – check package installation accuracy
- pkgrm – remove a package from the system
- plockstat – report user-level lock statistics
- pmadm – port monitor administration
- pmconfig – Configure the Power Management system
- pntadm – DHCP network table management utility
- pooladm – activate and deactivate the resource pools facility
- poolbind – bind processes, tasks, or projects or query binding of processes to resource pools
- poolcfg – create and modify resource pool configuration files
- poold – automated resource pools partitioning daemon
- poolstat – report active pool statistics
- ports – creates /dev entries and inittab entries for serial lines
- powerd – power manager daemon
- poweroff – stop the processor
- pppd – point to point protocol daemon
- pppoec – PPPoE chat utility
- pppoed – PPPoE server daemon
- pppstats – print PPP statistics
- pprosetup – setup program for Patch Manager
- pprosvc – automation service program for Patch Manager
- praudit – print contents of an audit trail file
- prctmp – shell procedures for accounting
- prdaily – shell procedures for accounting
- printmgr – Solaris Print Manager is a graphical user interface for managing printers in a network
- privatepw – administer FTP Server enhanced group access file
- prodreg – Solaris Product Registry administration
- projadd – administer a new project on the system
- projdel – delete a project from the system
- projmod – modify a project's information on the system
- prstat – report active process statistics
- prtacct – shell procedures for accounting
- prtconf – print system configuration
- prtdiag – display system diagnostic information
- prtfru – print FRUID-specific information about the FRUs on a system or domain
- prtpicl – print PICL tree
- prtvtoc – report information about a disk geometry and partitioning
- psradm – change processor operational status
- psrinfo – displays information about processors
- psrset – creation and management of processor sets
- putdev – edits device table
- putdgrp – edits device group table
- pwck – password/group file checkers
- pwconv – installs and updates /etc/shadow with information from /etc/passwd
- quot – summarize file system ownership
- quota – display a user's ufs file system disk quota and usage
- quotacheck – ufs file system quota consistency checker
- quotaoff – turn ufs file system quotas on and off
- quotaon – turn ufs file system quotas on and off
- raidctl – RAID hardware utility
- ramdiskadm – administer ramdisk pseudo device
- rarpd – DARPA Reverse Address Resolution Protocol server
- rcapadm – configure resource capping daemon
- rcapd – resource cap enforcement daemon
- rctladm – display or modify global state of system resource controls
- rdate – set system date from a remote host
- rdisc – network router discovery daemon
- reboot – restart the operating system
- reject – accept or reject print requests
- rem_drv – remove a device driver from the system
- removef – remove a file from software database
- repquota – summarize quotas for a ufs file system
- re-preinstall – installs the JumpStart software on a system
- restricted_shell – restricted shell command interpreter
- rexd – RPC-based remote execution server
- rexecd – remote execution server
- rlogind – remote login server
- rm_install_client – scripts used to install the Solaris software
- rmmount – removable media mounter for CD-ROM, floppy, Jaz drive, and others
- rmt – remote magtape protocol module
- rndc – name server control utility
- rndc-confgen – rndc key generation tool
- roleadd – administer a new role account on the system
- roledel – delete a role's login from the system
- rolemod – modify a role's login information on the system
- root_archive – manage bootable miniroot archives
- route – manually manipulate the routing tables
- routeadm – IP forwarding and routing configuration
- routed – network routing daemon
- rpc.bootparamd – boot parameter server
- rpc.mdcommd – multi-node disk set services
- rpc.metad – remote metaset services
- rpc.metamedd – remote mediator services
- rpc.metamhd – remote multihost disk services
- rpc.nisd – NIS+ service daemon
- rpc.nisd_resolv – NIS+ service daemon
- rpc.nispasswdd – NIS+ password update daemon
- rpc.rexd – RPC-based remote execution server
- rpc.rstatd – kernel statistics server
- rpc.rusersd – network username server
- rpc.rwalld – network rwall server
- rpc.smserverd – removable media device server
- rpc.sprayd – spray server
- rpc.yppasswdd – server for modifying NIS password file
- rpc.ypupdated – server for changing NIS information
- rpcbind – universal addresses to RPC program number mapper
- rpcinfo – report RPC information
- rpld – Network Booting RPL (Remote Program Load) Server
- rquotad – remote quota server
- rsh – restricted shell command interpreter
- rshd – remote shell server
- rstatd – kernel statistics server
- rtc – provide all real-time clock and GMT-lag management
- rtquery – query routing daemons for their routing tables
- runacct – run daily accounting
- rusersd – network username server
- rwall – write to all users over a network
- rwalld – network rwall server
- rwhod – system status server
- sa1 – system activity report package
- sa2 – system activity report package
- sac – service access controller
- sacadm – service access controller administration
- sadc – system activity report package
- saf – Service Access Facility
- sar – system activity report package
- savecore – save a crash dump of the operating system
- scadm – administer System Controller (SC)
- sckmd – Sun Fire High-End system key management daemon
- sconadm – register system information
- sendmail – send mail over the internet
- setuname – change machine information
- setup_install_server – scripts used to install the Solaris software
- sf880drd – Sun Fire 880 Dynamic Reconfiguration daemon
- sftp-server – SFTP server subsystem
- share – make local resource available for mounting by remote systems
- share_nfs – make local NFS file systems available for mounting by remote systems
- shareall – share, unshare multiple resources
- showmount – show remote mounts
- showrev – show machine, software revision, and patch revision information
- shutacct – shell procedures for accounting
- shutdown – shut down system, change system state
- slpd – Service Location Protocol Daemon
- smartcard – configure and administer a smart card
- smattrpop – populate security attribute databases in a name service
- smc – start the Solaris Management Console
- smccompile – build class list and compile Solaris Management Console service beans for remote use
- smcconf – configure the Solaris Management Console
- smcregister – configure the Solaris Management Console
- smcron – manage jobs in the crontab database
- smcwebserver – manage the server for the Sun Web Console
- smdiskless – manage diskless client support for a server
- smexec – manage entries in the exec_attr database
- smgroup – manage group entries
- smlog – manage and view WBEM log files
- smmaillist – manage email alias entries
- smmultiuser – manage bulk operations on user accounts
- smosservice – manage OS services
- smpatch – download, apply, and remove updates
- smprofile – manage profiles in the prof_attr and exec_attr databases
- smreg – register objects for the Sun Web Console
- smrole – manage roles and users in role accounts
- smrsh – restricted shell for sendmail
- smserialport – manage serial port
- smuser – manage user entries
- snmpbulkget – communicate with a network entity using SNMP GETBULK requests
- snmpbulkwalk – communicate with a network entity using SNMP BULK requests
- snmpcmd – commands to communicate with a network entity using SNMP requests
- snmpconf – creates and modifies SNMP configuration files
- snmpd – daemon to respond to SNMP request packets
- snmpdelta – monitor deltas of integer valued SNMP variables
- snmpdf – get a listing of disk space usage on a remote machine by means of SNMP
- snmpdx – Sun Solstice Enterprise Master Agent
- snmpget – communicate with a network entity using SNMP GET requests
- snmpgetnext – communicate with a network entity using SNMP GETNEXT requests
- snmpinform – send an SNMP trap to a manager
- snmpnetstat – show network status using SNMP
- snmpset – communicate with a network entity using SNMP SET requests
- snmptable – obtain and display an SNMP table
- snmptest – communicate with a network entity using SNMP requests
- snmptranslate – translate SNMP OID values into a more useful form
- snmptrap – send an SNMP trap to a manager
- snmptrapd – receive and log SNMP trap messages
- snmpusm – create and maintain SNMPv3 users on a remote entity
- snmpvacm – perform maintenance on an SNMP agent's View-based Access Control Module (VACM) table
- snmpwalk – communicate with a network entity using SNMP GETNEXT requests
- snmpXdmid – Sun Solstice Enterprise SNMP-DMI mapper subagent
- snmpXwbemd – SNMP Adapter Subagent for WBEM
- snoop – capture and inspect network packets
- soconfig – configure transport providers for use by sockets
- soladdapp – add an application to the Solstice application registry
- soldelapp – remove an application from the Solstice application registry
- solstice – access system administration tools with a graphical user interface
- sppptun – PPP tunneling driver utility
- spray – spray packets
- sprayd – spray server
- sshd – secure shell daemon
- ssh-keysign – ssh helper program for host-based authentication
- startup – shell procedures for accounting
- statd – network status monitor
- stmsboot – administration program for the Solaris I/O multipathing feature
- strace – print STREAMS trace messages
- strclean – STREAMS error logger cleanup program
- strerr – STREAMS error logger daemon
- sttydefs – maintain line settings and hunt sequences for TTY ports
- su – become superuser or another user
- sulogin – access single-user mode
- suninstall – install the Solaris operating system
- SUNWafb_config – configure the AFB Graphics Accelerator
- SUNWffb_config – configure the FFB Graphics Accelerator
- SUNWgfb_config – fbconfig module for configuring Sun XVR-1000 Graphics Accelerator
- SUNWifb_config – configure the Sun Expert3D Graphics Accelerator
- SUNWjfb_config – fbconfig module for configuring the Sun XVR-600 and XVR-1200 Graphics Devices
- SUNWkfb_config – fbconfig module for configuring the Sun XVR-2500 Graphics Device
- SUNWm64_config – configure the M64 Graphics Accelerator
- SUNWpfb_config – fbconfig module for configuring Sun XVR-100 Graphics Accelerator
- SUNWzulu_config – fbconfig module for configuring SunXVR-4000 Graphics Accelerator
- svc.configd – Service Management Facility repository daemon
- svc.startd – Service Management Facility master restarter
- svcadm – manipulate service instances
- svccfg – import, export, and modify service configurations
- swap – swap administrative interface
- sync – update the super block
- syncinit – set serial line interface operating parameters
- syncloop – synchronous serial loopback test program
- syncstat – report driver statistics from a synchronous serial link
- sysdef – output system definition
- syseventadm – sysevent event specification administration
- syseventconfd – kernel system event command invocation daemon
- syseventd – kernel system event notification daemon
- sysidconfig – execute system configuration applications, or define set of system configuration applications
- sysidnet – system configuration
- sysidnfs4 – system configuration
- sysidns – system configuration
- sysidpm – system configuration
- sysidroot – system configuration
- sysidsys – system configuration
- sysidtool – system configuration
- syslogd – log system messages
- sys-unconfig – undo a system's configuration
- talkd – server for talk program
- tapes – creates /dev entries for tape drives attached to the system
- taskstat – prints ASET tasks status
- tcxconfig – configure default linearity of 24-bit TrueColor Visual for OpenWindows
- telinit – process control initialization
- telnetd – DARPA TELNET protocol server
- tftpd – Internet Trivial File Transfer Protocol server
- th_define – create fault injection test harness error specifications
- th_manage – manage the fault injection test harness
- tic – terminfo compiler
- tnamed – DARPA trivial name server
- traceroute – print the route packets take to network host
- trapstat – report trap statistics
- TSIgfxp_config – configure the PGX32 (Raptor GFX) Graphics Accelerator
- ttyadm – format and output port monitor-specific information
- ttymon – port monitor for terminal ports
- tunefs – tune an existing UFS file system
- turnacct – shell procedures for accounting
- tzselect – select a time zone
- uadmin – administrative control
- ufsdump – incremental file system dump
- ufsrestore – incremental file system restore
- umount – mount or unmount file systems and remote resources
- umountall – mount, unmount multiple file systems
- unlink – link and unlink files and directories
- unshare – make local resource unavailable for mounting by remote systems
- unshare_nfs – make local NFS file systems unavailable for mounting by remote systems
- unshareall – share, unshare multiple resources
- update_drv – modify device driver attributes
- updatemanager – start the Sun Update Manager application
- useradd – administer a new user login on the system
- userdel – delete a user's login from the system
- usermod – modify a user's login information on the system
- utmp2wtmp – overview of accounting and miscellaneous accounting commands
- utmpd – utmpx monitoring daemon
- uucheck – check the uucp directories and permissions file
- uucico – file transport program for the uucp system
- uucleanup – uucp spool directory clean-up
- uucpd – UUCP server
- uusched – uucp file transport program scheduler
- Uutry – attempt to contact remote system with debugging on
- uutry – attempt to contact remote system with debugging on
- uuxqt – execute remote command requests
- vmstat – report virtual memory statistics
- volcopy – make an image copy of file system
- volcopy_ufs – make an image copy of a ufs file system
- vold – Volume Management daemon to manage removable media devices
- wall – write to all users
- wanboot_keygen – create and display client and server keys for WAN booting
- wanboot_keymgmt – insert and extract keys
- wanboot_p12split – split a PKCS #12 file into separate certificate and key files
- wanbootutil – manage keys and certificates for WAN booting
- wbemadmin – start Sun WBEM User Manager
- wbemconfig – convert a JavaSpaces datastore to the newer Reliable Log datastore format
- wbemlogviewer – start WBEM Log Viewer
- whodo – who is doing what
- wracct – write extended accounting records for active processes and tasks
- wrsmconf – manage WCI RSM controller configurations
- wrsmstat – report WCI RSM driver statistics
- wtmpfix – manipulate connect accounting records
- xntpd – Network Time Protocol daemon
- xntpdc – special NTP query program
- ypbind – NIS binder process
- ypinit – set up NIS client
- ypmake – rebuild NIS database
- ypmap2src – convert NIS maps to NIS source files
- yppasswdd – server for modifying NIS password file
- yppoll – return current version of a NIS map at a NIS server host
- yppush – force propagation of changed NIS map
- ypserv – NIS server and binder processes
- ypset – point ypbind at a particular server
- ypstart – Start and stop NIS services
- ypstop – Start and stop NIS services
- ypupdated – server for changing NIS information
- ypxfr – transfer NIS map from a NIS server to host
- ypxfr_1perday – transfer NIS map from a NIS server to host
- ypxfr_1perhour – transfer NIS map from a NIS server to host
- ypxfr_2perday – transfer NIS map from a NIS server to host
- ypxfrd – NIS server and binder processes
- zdb – ZFS debugger
- zdump – time zone dumper
- zfs – configures ZFS file systems
- zic – time zone compiler
- zoneadm – administer zones
- zoneadmd – zone administration daemon
- zonecfg – set up zone configuration
- zpool – configures ZFS storage pools
- zuludaemon – load microcode for Sun XVR-4000 Graphics Accelerator device
 The Early Days of PHP
The Early Days of PHP







