 Not many posts in the past couple of weeks. Is this the feeling you get? You can be quite right about this. I have been on a short, hiking with my girlfriend at La-Palma. We have been waling the mountains of La-Palma, been sleeping in the sun, relaxing and we have found some time to bring a visit to Instituto de Astrofísica de Canarias.
Not many posts in the past couple of weeks. Is this the feeling you get? You can be quite right about this. I have been on a short, hiking with my girlfriend at La-Palma. We have been waling the mountains of La-Palma, been sleeping in the sun, relaxing and we have found some time to bring a visit to Instituto de Astrofísica de Canarias.
Also in the week after the trip I still had a week of holidays left which I spend for looking for a new job. This was with some success which resulted in the fact that I have resigned from my current job as Technical Oracle Consultant at Canon Europe and I have accepted a new job at an Oracle consultancy firm as a consultant.
I have had a splendid time at Canon Europe and I was able to be part of the Canon Tri.Can and travel around in Europe from time to time. However I have decided that it is time to make a change as my current team is been divided and we will no longer be able to work as a single team, we will become some sort of virtual team under different managers and I feel I will not be able to feel at home anymore when this change comes in places. To read more about the Tri.Can project you can turn to one of the contracting companies their website to find out more.
 Inventory Management is always a big issue, what do we have on stock, what do we need to order, what item is located where. This is the case for major companies, a simple household and even for the international space station ISS . Due to the volume of articles onboard Station, and the fact that Station will be on orbit continuously for at least 15 years, the need arises for a system of tracking the location and status of items that have been stored on board. The Inventory Management System (IMS) fulfills that purpose.
Inventory Management is always a big issue, what do we have on stock, what do we need to order, what item is located where. This is the case for major companies, a simple household and even for the international space station ISS . Due to the volume of articles onboard Station, and the fact that Station will be on orbit continuously for at least 15 years, the need arises for a system of tracking the location and status of items that have been stored on board. The Inventory Management System (IMS) fulfills that purpose.
This application is based on the use of barcode labels. Starting in March 2007, the old barcode reader terminals will be replaced by PDAs. These PDAs will be equipped with a barcode reader and will be connected to the IMS via a wireless network.
In the near future, PDAs will start being used as integrated components of the IMS.
A special application, known as the PDA Depressurisation Program (PDP) and conceived by the astronaut Thomas Reiter, has been developed by ESA to compute the ‘egress time’, – the time that is left before having to abandon the ISS in the event of depressurisation.
This application, tested for usability by Reiter during his long duration mission – from July to December 2006 – is currently undergoing qualification by NASA and will become part of the standard set of software packages loaded on each astronaut PDA.
PDAs have been investigated as alternative or complementary platforms for some of the applications currently running on the ISS laptops. The idea is to use a PDA in those situations where a laptop might be inconvenient because it is too big or cumbersome.
An example of laptop to PDA conversion, developed by industry using ESA research and development funding, is the porting of the ESA/NASA International Procedure Viewer (IPV) application. In this type of conversion, the critical factor is adapting the laptop based user interface to a new platform where the available screen area is significantly smaller.
Another area of research is the use of the PDA as a voice or speech processing platform. Combined with wireless communication, PDAs could become suitable devices for crew-to-crew communication (VOIP applications) and crew-to-system communication (speech synthesis and speech recognition One limitation for applications employing voice sounds for either input or output is the noise that is always present on board the ISS, most of which is generated by the ventilation system. The PDA Depressurization Program uses speech synthesis to notify the crew members about the time remaining before egress. However, ambient sound is not an issue for this application because, if depressurization occurs, the ventilation system is automatically switched off as safety measure.

The Hubble Space Telescope’s primary camera is offline, with some science capabilities likely lost for good, NASA officials said Monday.
An electrical short in the backup system for Hubble’s Advanced Camera for Surveys (ACS) pushed the space telescope into a protective “safe mode” over the weekend and prompted the formation of an Anomaly Investigation Board on Monday, NASA officials said.
The incident, the third since June to hobble Hubble’s ACS camera, occurred at 7:34 a.m. EST (1234 GMT) on Jan. 27. Engineers managed to switch the space telescope back to normal operations, with the exception of the ACS instrument, by Sunday and hope to resume science observations with the observatory’s remaining instruments later this week.
NASA has convened an Anomaly Review Board to go over Hubble’s latest malfunction, the results of which are expected to be presented by March 2.
“Obviously, we are very disappointed by this latest event because of the popularity of the ACS instrument with astronomers,” NASA’s Preston Burch, Hubble program manager at the Goddard Space Flight Center (GSFC) in Greenbelt, Maryland, told reporters today in a teleconference.
It was Hubble’s ACS camera’s wide field channel, for example, that allowed astronomers to generate Hubble’s Ultra Deep Field – the deepest view into the universe to date. But that ACS channel, and a high-resolution channel used to study stars surrounded by planet-forming material, are likely lost since the latest glitch has cut off power to their systems, Hubble managers said.
“We’re not optimistic at all that those will be restored,” said David Leckrone, NASA’s senior project scientist for Hubble at the GSFC. “The saving grace here is that we have a superb new wide field camera coming along that was originally designed, in fact, to be a back up for ACS in case ACS failed. It was designed to work in tandem with ACS if [it] was full alive.”
That new camera – known as Wide Field Camera 3 – is due to be installed at Hubble during NASA’s last space shuttle flight to the observatory in September 2008.
Hubble engineers hope they will be able to restore partial ACS science capability with its third feature – the Solar Blind channel used recently to study auroras on Jupiter and Saturn – by February to aid NASA’s New Horizons mission, which is due to make a close flyby of Jupiter on Feb. 28.
“As soon as we’re confident that everyone has done their homework on that, we could very have the Solar Blind operating by the end of February,” Burch said. “That would be the hope.”
Hubble’s other, non-ACS instruments – the Field Planetary Camera 2, Near Infrared Camera Multi-Object Spectrograph, and the Fine Guidance Sensors – are unaffected by the recent glitch.
Hubble’s camera troubles
Hubble’s ACS camera has been working on its backup, or Side B, system since the instrument’s primary Side A electronics encountered a malfunction in June 2006. An electronics hiccup a few months later in September again knocked the camera offline, but the system recovered a short time later.
NASA Hubble managers said the most recent glitch is a completely isolated incident and is not connected to the earlier problems.
“It’s very different,” Burch said, adding that the current anomaly’s signature is very different from those seen last year.
Hubble managers have also prepared about six observation surveys that do not require the ACS camera just in case the finicky instrument went offline. Those research projects will now be implemented while the camera is unavailable.
The ACS anomaly comes just two months before the instrument’s projected five-year warranty expired, Hubble managers said. Spacewalking astronauts installed the camera on March 7, 2002 during NASA’s STS-109 mission aboard the Columbia orbiter. Launched in 1990, the Hubble Space Telescope has been billed as one of the most valuable astronomical instruments of all time and is the product of a partnership between NASA and the European Space Agency.
“It’s certainly been an astounding success as an instrument,” Rick Howard, acting director of NASA’s Astrophysics Division at NASA’s headquarters in Washington, D.C., adding that the camera met about all of its initial science objectives before its recent failure.
Because of the ACS camera’s hard-to-reach location on Hubble and the already packed five-spacewalk schedule of NASA’s final servicing mission to Hubble – Servicing Mission 4 slated to launch in September 2008 – adding a new and complicated repair job to the spaceflight is not an attractive option, Burch said.
“Servicing Mission 4 is a very full mission with installing new batteries and gyroscopes, installing one of the fine guidance sensors and two new instruments,” Burch said, adding that the initial plan carries no ACS-related additions to the upcoming Hubble overhaul.
Leckrone said that the new instruments to be grafted into Hubble during Servicing Mission 4 (SM-4) will almost completely restore the telescope’s lost ACS abilities, though the new Wide Field Camera 3 will take longer to generate its predecessor’s stunning views of the universe.
“The successful completion of SM-4 and insertion of Wide Field Camera 3 will take us fully back to not only where we are now, but where we want [Hubble] to be in the future,” Leckrone said.
Concurrent request in Oracle can be compared with Cron Jobs under UNIX. They give you the possibility to schedule programs to run once or periodically. The power of a concurrent request is that it will run inside your database application. The power of this is that you can do all your coding and scheduling inside your database without the need to create a external program which will call your database application and perform the requested tasks.
Concurrent requests are often used to periodically check things, clean-up stuff, export information or forward data. To create and schedule a concurrent request in Oracle Applications you basically need to complete those five steps:
(1) Create your code.
(2) Define a Concurrent Program Executable.
(3) Define a Concurrent Program.
(4) Attach to a Request Group.
(5) Schedule the Concurrent Request.
(1) Creating code:
As an example we will use a PL/SQL concurrent request, you can use other languages such as Java to create code, which can be called by a concurrent request however in this example we will only discuss a PL/SQL concurrent request.
When creating a PL/SQL procedure you can create this as you would normally create a stored procedure. The only difference is that you will need to create 2 OUT parameters, namely ERRBUF and RETCODE. This is required if you want to run the procedure as a concurrent request:
Example:
PROCEDURE mail_stuck_orders(errbuf out varchar2, retcode out number)
IS
……….
For more information about how to create a concurrent request you can refer to the Oracle Applications Developer’s guide.
(2) Define a Concurrent Program Executable.
To be able to use the code as a concurrent program you first have to define your code as a executable code in Oracle Applications. To do so select the “System Administrator” responsibility and go to the following menu: “Concurrent” : “Program” : “Executable”. As an example we are creating a program that will check if orders placed using Oracle iStore are stuck in a queue.
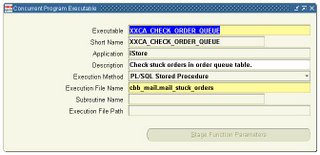 The minimal required information for defining a Concurrent Program Executable are:
The minimal required information for defining a Concurrent Program Executable are:
- Executable:
Enter a name for your concurrent program executable. In the Concurrent Programs window, you assign this name to a concurrent program to associate your concurrent program with your executable logic.
- Short name:
Enter a short name for your concurrent program executable.
- Application:
The concurrent managers use the application to determine in which directory structure to look for your execution file.
- Execution Method:
The possible execution methods are:
* Host: The execution file is a host script.
* Oracle Reports: The execution file is an Oracle Reports file.
* PL/SQL Stored Procedure: The execution file is a PL/SQL stored procedure.
* Java Stored Procedure: The execution file is a Java stored procedure.
* Java Concurrent Program: The execution file is a program written in Java.
* Multi Language Function: The execution file is a function (MLS function) that supports running concurrent programs in multiple languages.
* SQL*Loader: The execution file is a SQL script.
* SQL*Plus: The execution file is a SQL*Plus script.
* Spawned: The execution file is a C or Pro*C program.
* Immediate: The execution file is a program written to run as a subroutine of the concurrent manager. We recommend against defining new immediate concurrent programs, and suggest you use either a PL/SQL Stored Procedure or a Spawned C Program instead.
* Request Set Stage Function: PL/SQL Stored Function that can be uesd to calculate the completion statuses of request set stages.
- Execution File Name:
Enter the operating system name of your execution file. Some operating systems are case sensitive, so the name entered here should match the file name exactly. Do not include spaces or periods (.) in the execution file name, unless the execution method is PL/SQL stored procedure or Request Set Stage Function. The maximum size of an execution file name is 60 characters.
An option are the following 2 fields:
- Subroutine Name:
Enter the name of your C or Pro*C program subroutine here. Do not use spaces or periods (.) in this field. Only immediate programs or spawned programs using the Unified C API use the subroutine field. We recommend against defining new immediate concurrent programs, and suggest you use either a PL/SQL Stored Procedure or a Spawned C Program instead.
- Stage Function Parameters: The Stage Function Parameters button opens a window that allows you to enter parameters for the Request Set Stage Function. This button is only enabled when you select Request Set Stage Function as your Execution Method.
(3)Define a Concurrent Program.
The following step is to create a program and link this to the newly created executable. The following fields and options are available when defining a Concurrent Program:
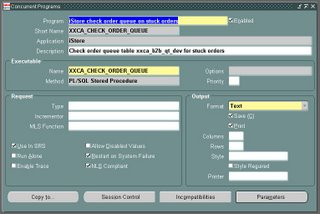 - Concurrent Programs Block:
- Concurrent Programs Block:
The combination of application name plus program name uniquely identifies your concurrent program.
- Program:
You see this longer, more descriptive name when you view your requests in the Requests window. If this concurrent program runs through Standard Request Submission, you see this name in the Submit Requests window when you run this program.
- Short Name:
Enter a brief name that Oracle Applications can use to associate your concurrent program with a concurrent program executable.
- Application:
The program's application determines what ORACLE username your program runs in and where to place the log and output files.
- Enabled:
Indicate whether users should be able to submit requests to run this program and the concurrent managers should be able to run your program. Disabled programs do not show up in users' lists, and do not appear in any concurrent manager queues. You cannot delete a concurrent program because its information helps to provide an audit trail.
Executable.
- Name:
Select the concurrent program executable that can run your program. You define the executable using the Concurrent Program Executables window. You can define multiple concurrent programs using the same concurrent program executable. See: Concurrent Program Executables.
- Options:
Some execution methods, such as Oracle Reports, support additional execution options or parameters. You can enter such options in this field. The syntax varies depending on the execution method. If you define a concurrent program with the bitmapped version of Oracle Reports, you can control the orientation of the bitmapped report by passing the ORIENTATION parameter or token. For example, to generate a report with landscape orientation, specify the following option in the Options field:
ORIENTATION=LANDSCAPE
Do not put spaces before or after the execution options values. The parameters should be separated by only a single space. You can also specify an orientation of PORTRAIT.
You can control the dimensions of the generated output with the PAGESIZE parameter. A specified x in the Options field overrides the values specified in the report definition. For example:
ORIENTATION=LANDSCAPE PAGESIZE=8x11.5
The units for your width and height are determined by your Oracle Reports definition. You set the units in your Oracle Reports menu under Report => Global Properties => Unit of Measurement.
If the page size you specify with the PAGESIZE parameter is smaller than what the report was designed for, your report fails with a "REP-1212" error.
- Method:
The execution method your concurrent program uses appears here.
- Priority:
You can assign this program its own priority. The concurrent managers process requests for this program at the priority you assign here. If you do not assign a priority, the user's profile option Concurrent:Priority sets the request's priority at submission time.
- Request:
Type If you want to associate your program with a predefined request type, enter the name of the request type here. The request type can limit which concurrent managers can run your concurrent program.
- Incrementor:
For use by Oracle Applications internal developers only. The incrementor function is shown here.
- MLS Function:
The MLS function, if any, used by the program. The Multilingual Concurrent Request feature allows a user to submit a request once to be run multiple times, each time in a different language. If this program utilizes this feature the MLS function determines which installed languages are needed for the request.
- Use in SRS:
Check this box to indicate that users can submit a request to run this program from a Standard Request Submission window. If you check this box, you must register your program parameters, if any, in the Parameters window accessed from the button at the bottom of this window.
- Allow Disabled Values:
If you check the Use in SRS box, you can also check this box to allow a user to enter disabled or outdated values as parameter values.
Many value sets use special table columns that indicate whether a particular value is enabled (using ENABLED_FLAG, START_DATE_ACTIVE, and END_DATE_ACTIVE columns). These value sets normally allow you to query disabled or outdated values but not enter them in new data. For Standard Request Submission, this means that a user would not normally be allowed to enter disabled values as report parameter values when submitting a report, even if the report is a query-only type report.
- Run Alone:
Indicate whether your program should run alone relative to all other programs in the same logical database. If the execution of your program interferes with the execution of all other programs in the same logical database (in other words, if your program is incompatible with all programs in its logical database, including itself), it should run alone.
You can enter any specific incompatible programs in the Incompatible Programs windows.
- Enable Trace:
Turns on SQL tracing when program runs.
- Restart on System Failure:
Use this option to indicate that this concurrent program should automatically be restarted when the concurrent manager is restored after a system failure.
- NLS Compliant:
This box is checked if the program allows for a user to submit a request of this program that will reflect a language and territory that are different from the language and territory that the users are operating in.
For example, users can enter orders in English in the United Kingdom, using the date and number formats appropriate in the United Kingdom, then generate invoices in German using the date and number formats appropriate to their German customers.
If this box is left blank then a user can associate any installed language with the request, but the territory will default to the territory of the concurrent manager environment.
Note that this option should be set only by the developer of the program. The program must be written as NLS Compliant to utilize this feature. See: the Oracle Applications Developer's Guide.
Note that this option should be set only by the developer of the program. The program must be written as NLS Compliant to utilize this feature.
- Format:
Select the output format from the following: HTML, PCL (HP's Printer Control Language), PDF, PS (Post Script) and Text. Attention: If you choose HTML or PDF as the output type with Oracle Report programs, you must use an appropriate printer driver that handles HTML or PDF files.
- Save:
Indicate whether to automatically save the output from this program to an operating system file when it is run. This value becomes the default for all requests submitted for this program. The output of programs with Save set to No is deleted after printing.
If this is a Standard Request Submission program, users can override this value from the Submit Requests window.
- Print:
If you enter No, your concurrent program's output is never sent to the printer.
- Columns / Rows:
Enter the minimum column and row length for this program's report output. Oracle Applications uses this information to determine which print styles can accommodate your report.
- Style: The print style you select depends on your system and printer setup. Print styles include: 132 columns and 66 lines (Landscape), 180 columns and 66 lines (Landwide), 80 columns and 66 lines (Portrait), 132 columns and 62 lines (A4). Your list is limited to those styles that meet your program's columns and row length requirements.
- Style Required: If your program requires a specific print style (for example, a checkwriting report), use this check box to enforce that print style.
- Printer: If you want to restrict your program's output to a single printer, enter the name of the printer to which you want to send your output. If your program has minimum or maximum columns or rows defined, your list of values is limited to those printers that can support your program's requirements.
(4) Attach to a Request Group.
After creating your code, Defining a Concurrent Program Executable and defining a Concurrent Program you have to attaché it to a request group. This will handle the part where is decided who can run what, member of a request group can run the concurrent programs defined in the specified request group. You can access the Request Group screen at “Security” : “Responsibility” : “Request”.
Use this window to define a request group. A request security group is the collection of requests, request sets, and concurrent programs that a user, operating under a given responsibility, can select from the Submit Requests window.
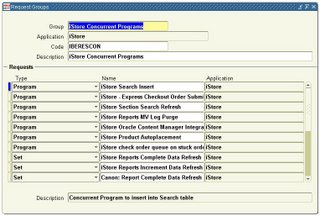 System Administrators:
System Administrators:
- Assign a request security group to a responsibility when defining that responsibility. A responsibility without a request security group cannot run any requests using the Submit Requests window.
- Can add any request set to a request security group. Adding a private request set to a request security group allows other users to run that request set using the Submit Requests window.
Users:
- Can create their own private request sets using the Request Sets window. In a private request set, users can include only the requests you assign to their request security group.
- Cannot update another user's private request set using the Request Sets window.
- Cannot delete a private request set if it is assigned to a request security group.
Request Groups Block
- Group: Use the request group's name to assign the request group to a responsibility on the Responsibilities window. An application name and request group name uniquely identify a request group.
- Application: Select the name of the application you wish to associate with your request group. An application name and a request security group name uniquely identify a request security group. This application name does not prevent you from assigning requests and request sets from other applications to this request group.
- Code: Assign a code to this request group. Some products use the request group code as a parameter that identifies the requests a customized standard submission form can select. See: Customizing the Submit Requests Window using Codes.
(5)Schedule the Concurrent Request.
After those steps your Concurrent Program can be used and scheduled. This was what it was all about. Now you can schedule it. You can schedule it to run once or every X time. You can see from the screenshots most of the options available to you.
You can access the scheduling screens by clicking “view” -> “requests”.
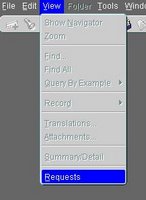
In the following screen you will be able to search for a request based upon a request ID and or one of the other fields available to you in the screen.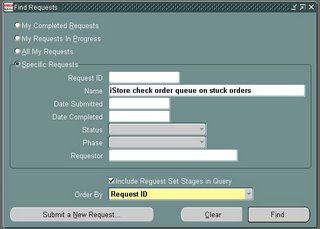 This will provide you with a good inside view to all your running, pending or completed requests.
This will provide you with a good inside view to all your running, pending or completed requests.
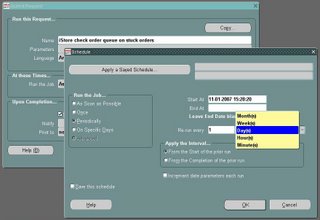
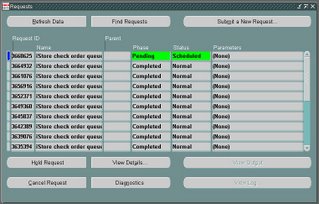 The following screen is showing you the options of scheduling a request.
The following screen is showing you the options of scheduling a request.
The first is about a Brazilian judge who decided that YouTube.com has to close if they not remove a adult video where you can watch Daniela Ciccarelli and her boyfriend Tato Malzoni making love on a Spanish beach. Google, the new owner of Youtube.com has already removed the video clip however every time they do so the YouTube community uploads a new video. The judge now decided that Google has to remove the video and make sure it cannot be replaced again.
How this will play out when Google is not complying with this can become interesting as the Google Holding is the owner of YouTube and this is a US based company and the verdict of the judge will only be valid in Brasilia.
The second problem Google is facing with YouTube is that several large production and broadcast companies are starting to sue YouTube because the copyrighted material. Several shows are published on YouTube, which are copyrighted. Because of this the companies demand a fine for every movie that is copyrighted and is published on YouTube, this could potentially lead to a total fine of a enormous amount if Google is not acting very fast now.
I have already reported about a security flaw in the way Oracle is working with the passwords stored for Oracle E-business suite. The passwords are stored in an encrypted form and not as a hash value. This means that if an entered password can be compared with a encrypted password there is somehow a function that allows you to decrypt a password.
After some research I found the decryption technique to be in APPLSYS. FND_WEB_SEC as an internal function used to decrypt the encrypted passwords. TO make the function available outside the package a single line of code needs to be added to FND_WEB_SEC.
After understanding the complete way the package was working it came to my attention that you are able to decrypt all user passwords in this way. Due to the possible security risks for companies and the possible difficulties this can cause for SOX (Sarbanes-Oxley) compliant companies I informed CERT and the Dutch CERT. CERT.org responded in a quick and good way. I received a ticket number and have been updated about all communication between CERT and Oracle. The Dutch version of CERT however informed me that they would contact Oracle and requested me to remove the information from my weblog. This was the only communication I ever received from the Dutch CERT.
CERT.org have been keeping me up-to-date and finally responded that they would NOT send out a warning as there is a rather high level of access needed to the system to make the change to the FND_WEB_SEC package. I can agree on this as we are talking from a production system point of view, however the exploit becomes more scary when you think about a development environment cloned from a production environment.
In this case a lot of developers will have the access rights to do so and will be able to lookup passwords and use this in the production environment. This is to say if the passwords are not reset. As most companies are unaware of this exploit, resetting the passwords is not a step taken in the cloning process of a production environment to a development environment.
Even do, I understand the standpoint of CERT.org however I do not understand the standpoint of Oracle who identified this as a very minor glitch in there security module. Personally I think this is a lot more than a minor glitch. Personally I think the complete security model is setup wrongly from the beginning by storing an encrypted password instead of a password hash value.
If some people like to gain some more insight in the way the security problem is working I have posted some code on my website terminalcult.org.
I have a uploaded a query which enables you to decrypt a password. And I created a Oracle function which will do the same, the function has some more details in it to start understanding the way the system works.
 Not many posts in the past couple of weeks. Is this the feeling you get? You can be quite right about this. I have been on a short, hiking with my girlfriend at La-Palma. We have been waling the mountains of La-Palma, been sleeping in the sun, relaxing and we have found some time to bring a visit to Instituto de Astrofísica de Canarias.
Not many posts in the past couple of weeks. Is this the feeling you get? You can be quite right about this. I have been on a short, hiking with my girlfriend at La-Palma. We have been waling the mountains of La-Palma, been sleeping in the sun, relaxing and we have found some time to bring a visit to Instituto de Astrofísica de Canarias.







